Introduction
In an era defined by rapid technological advancements and digital transformation, cloud computing has emerged as a cornerstone of modern enterprise infrastructure. However, navigating the complexities of cloud security, governance, and management requires a meticulous understanding of best practices and strategic frameworks. This article delves into the fundamental aspects of cloud security, offering insights into essential measures such as multi-factor authentication, encryption, and zero-trust models.
Additionally, it explores the significance of robust governance structures, the role of automation in enhancing efficiency, and the criticality of cost management and resource optimization.
The discussion extends to disaster recovery strategies, emphasizing the need for comprehensive planning and regular testing to ensure business continuity. Furthermore, it highlights the importance of cultivating strong vendor relationships and the indispensable role of continuous employee training in leveraging cloud technologies effectively. As organizations increasingly adopt hybrid and multi-cloud strategies, this article provides a trusted guide to navigating the evolving cloud landscape, ensuring security, efficiency, and innovation.
Understanding Cloud Security Fundamentals
Creating a strong protective structure is essential for safeguarding cloud-based applications and data. Organizations should integrate multi-factor authentication, encryption, and secure access protocols to mitigate risks. Regular safety inspections and vulnerability evaluations are essential for identifying potential threats. Implementing a zero-trust framework ensures that all users, whether internal or external, are treated as potential threats until verified.
Identity and Access Management (IAM) plays a critical role in this process, providing a dynamic landscape that adapts to modern cybersecurity challenges. Successful IAM implementation establishes a secure, efficient, and scalable digital environment. For instance, Role-Based Access Control (RBAC) allows entities to control and monitor access based on employee roles, ensuring that individuals can only access areas relevant to their responsibilities. This approach is akin to managing access in a multi-floor office building, where each floor hosts different departments and sensitive information, and employees are granted access based on their roles.
The significance of a comprehensive protection strategy is highlighted by recent trends in cloud safety. A survey of 927 cybersecurity professionals worldwide revealed that 78% of organizations are adopting hybrid and multi-cloud strategies. These strategies require strong protective measures to safeguard valuable digital assets across diverse environments. 'Despite the maturity of the online services market, the need for vigilant security practices remains paramount, as evidenced by the continued focus on External Attack Surface Management (EASM) and the evolving threat landscape.'.
Cloud Governance and Management
Effective governance frameworks are essential for managing online operations efficiently. This involves clearly defining roles and responsibilities, establishing comprehensive policies for online resource usage, and setting precise performance metrics. With the implementation of a robust cloud management platform, organizations can standardize processes and gain visibility across multiple cloud environments. This not only enhances decision-making but also ensures compliance with regulatory requirements.
In today's data-driven world, protecting sensitive information is paramount. Governance frameworks must include policies for information privacy and security, such as encryption, access controls, and regular audits. For instance, sectors such as healthcare and finance have stringent regulations to protect user information. 'Cloud providers supply the infrastructure, but adherence to these regulations remains the duty of the entity.'.
Furthermore, efficient governance tackles shared issues such as restricted resources and isolated information. By demonstrating the return on investment (ROI) and emphasizing benefits such as improved data quality and compliance, entities can secure necessary resources. This approach fosters a culture of data-driven decision-making and ensures sustained performance and innovation.
Automation and Efficiency in Cloud Management
Automation tools are pivotal in enhancing operational efficiency within cloud environments. Leveraging Infrastructure as Code (IAC) and Continuous Integration/Continuous Deployment (CI/CD) pipelines allows organizations to streamline deployment processes, ensuring consistency and minimizing manual errors. For instance, adopting IAC solutions like Terraform can simplify and standardize infrastructure configuration, enabling companies to scale with minimal effort. Delivery Hero’s IT team tackled the challenge of employee account lockouts by automating their recovery process, significantly reducing downtime and boosting productivity.
In the fast-paced realm of software development, DevOps practices have revolutionized the industry by fostering continuous improvement and rapid deployment. Automation, central to DevOps, closes the gaps between development, operations, and quality assurance, aligning with business goals for faster delivery and improved accuracy. The integration of Generative IAC with Artificial Intelligence (AI) further enhances this, automating the generation of IAC scripts based on system requirements and past data patterns.
As businesses navigate this evolving landscape, regularly reviewing and optimizing automated workflows is crucial. This ensures alignment with changing business needs and leverages the latest advancements in automation technology, such as AI-driven code completions in integrated development environments (IDEs). These advancements not only accelerate the software delivery process but also enhance developer productivity, as evidenced by tools like GitHub Copilot. By focusing on innovation and strategic tasks, teams can drive significant value and maintain a competitive edge.
Cost Management and Resource Optimization
Monitoring cloud spending is essential for maintaining budget control and optimizing resource utilization. Implementing advanced tools that provide visibility into resource usage and cost trends can significantly enhance this process. According to the latest updates from Microsoft Cost Management, these tools can help organizations better understand where costs are accruing, identify inefficient spending patterns, and optimize expenses to achieve more with less.
By conducting thorough data analysis and showback, stakeholders can gain insights into how resources are being utilized across various departments and projects. This transparency not only aids in tracking cost trends but also enables informed decision-making regarding resource allocation and optimization. For example, the Infoblox report highlights that users of their solutions saw a 75% increase in operational efficiency and a 79% reduction in operational costs.
Implementing a thorough cost management strategy for online services is essential for predicting expenses and preventing unforeseen fees. Enterprises need to incorporate both cost and carbon emissions into their operational goals, continuously monitor progress, and establish governance mechanisms. This approach aligns with the broader definition of responsible technology, which emphasizes minimizing both financial and environmental impacts while maximizing business value.
Moreover, comprehending pricing structures for online services is essential. Prices are applied to Stock Keeping Units (SKUs), which can be either list prices or contracted/custom prices. Familiarizing oneself with these models allows for better cost optimization. As the demand for SaaS products continues to rise, particularly among SMEs, the ability to predict and control online service spending becomes increasingly important. Overall, these strategies empower IT decision-makers to drive innovation and maintain competitive advantage in a rapidly evolving digital landscape.
Disaster Recovery and Backup Strategies
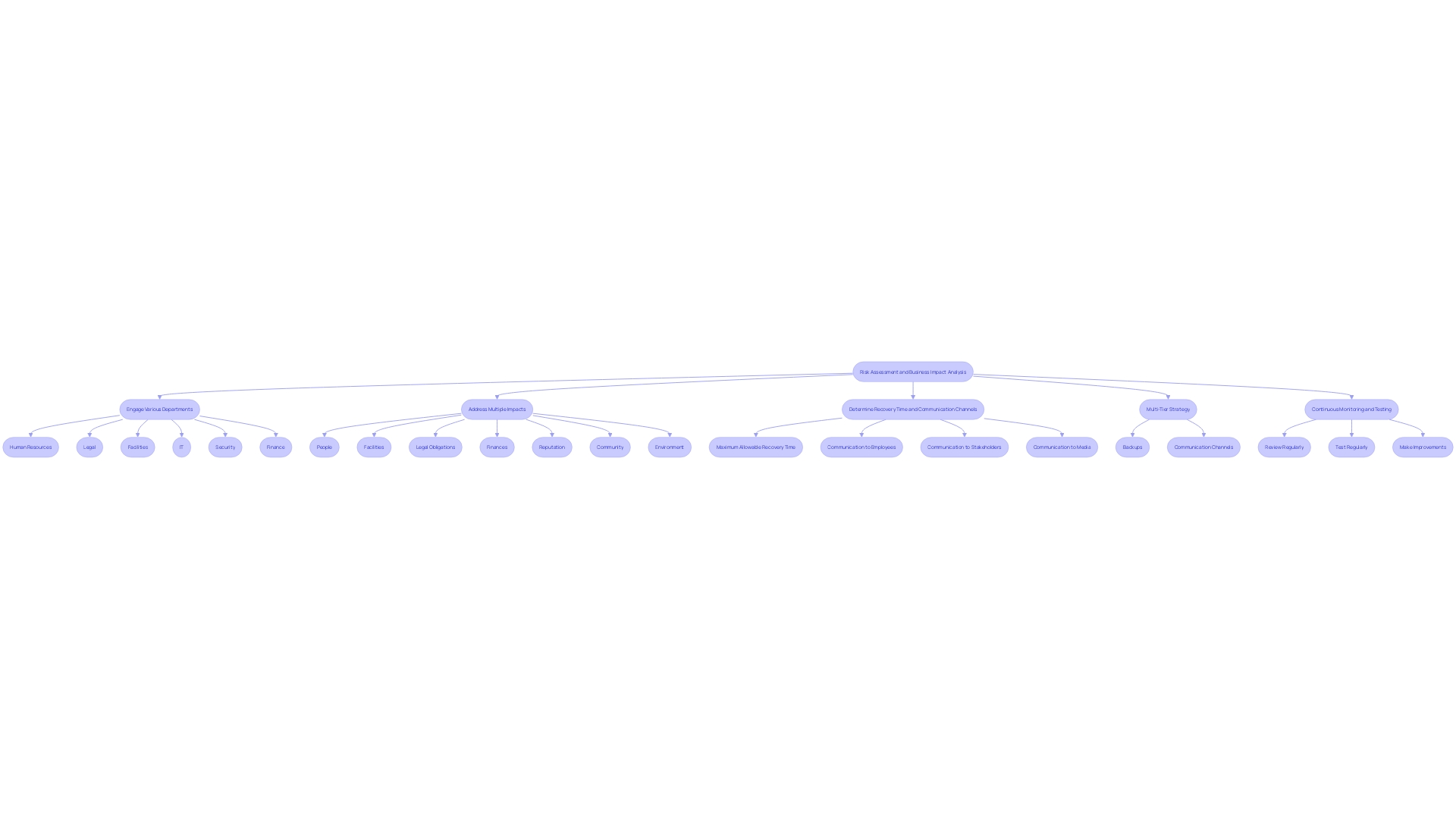
A comprehensive disaster recovery plan is vital for maintaining business continuity during a failure. The process commences with a thorough risk assessment and business impact analysis, aligning with organizational objectives. Engage personnel from various departments such as human resources, legal, facilities, IT, security, and finance in the planning stages. The plan should address impacts on people, facilities, legal obligations, finances, reputation, the community, and the environment.
Organizations should adopt a multi-tier strategy that includes regular backups, geographic redundancy, and automated failover processes. Determining the maximum allowable recovery time and establishing clear communication channels for employees, stakeholders, and the media is crucial. Once implemented, it’s essential to continuously monitor, review, and test the recovery plans, making necessary improvements to ensure their effectiveness and swift execution when needed. Regular testing and updates will help keep the disaster recovery plan robust and reliable.
Vendor Relationship Management and Collaboration
Developing strong connections with service providers is crucial for optimizing value and guaranteeing smooth operations. Effective engagement involves regular communication to align on service expectations and performance metrics, fostering a collaborative environment. One way to solidify this relationship is through the establishment of comprehensive Service Level Agreements (SLAs), which delineate clear support and escalation procedures.
Research indicates that the success of digital procurement initiatives is not solely dependent on technology, but rather on the quality of stakeholder communication and collaboration. This underscores the importance of ongoing dialogue with service providers to preemptively address potential issues and ensure mutual understanding.
In addition, data from over 1,000 companies using the Common Paper platform highlights the importance of well-structured agreements. Such agreements provide clarity on terms and conditions, which is vital for accountability and consistent service delivery. By concentrating on these elements, organizations can improve their investments in online services and drive technological innovation effectively.
Employee Training and Continuous Improvement
To maximize the advantages of online technologies, ongoing employee training is essential. Organizations should invest in comprehensive training programs that cover essential concepts, best practices for protection, and the specific tools used within their online infrastructure. By promoting an environment of ongoing education, teams can remain updated on the newest developments in technology and methodologies. This proactive approach not only enhances skills but also ensures alignment with industry standards and best practices, significantly mitigating potential security risks.
A case in point is Nets, a leading provider of digital payment solutions. With over 50 years in the industry, Nets has successfully navigated the complexities of cloud adoption by prioritizing employee training. Their structured onboarding process has yielded positive results, ensuring that new starters are equipped with the necessary skills to handle cloud-based tools and technologies effectively. As one project leader at Nets noted, transforming technical data into engaging and easily understandable formats was crucial in motivating users to explore and utilize the information independently.
Moreover, according to the 2023 Lean into Learning Report, understanding the evolving workforce and the essential skills needed in today’s digital landscape is vital. The report emphasizes that a robust training strategy is a cornerstone for achieving holistic workforce transformation. With three-quarters of safety experts recognizing the present threat environment as the most difficult in the last five years, it becomes essential for companies to guarantee their teams are well-prepared and resilient.
In summary, continuous training and development in cloud technologies are not just beneficial but necessary for any entity looking to thrive in the digital age. By investing in comprehensive training programs, fostering a culture of continuous improvement, and staying updated with the latest advancements, organizations can significantly enhance their operational efficiency and security posture.
Conclusion
A robust cloud security framework is essential for protecting digital assets, incorporating key measures such as multi-factor authentication, encryption, and a zero-trust model. Effective Identity and Access Management (IAM) enhances security by controlling access based on user roles, particularly as organizations embrace hybrid and multi-cloud strategies.
Governance and management are critical for standardizing processes and ensuring regulatory compliance. Clearly defined roles and comprehensive policies foster a culture of data-driven decision-making while addressing challenges like siloed data.
Automation significantly improves operational efficiency through tools like Infrastructure as Code (IaC) and CI/CD pipelines, which streamline deployment and reduce errors. Regularly reviewing these automated workflows ensures they align with evolving business needs.
Cost management is vital for financial sustainability. Advanced monitoring tools enhance visibility into spending, while understanding cloud pricing models aids in optimizing expenses.
A comprehensive disaster recovery plan is crucial for business continuity, involving multi-tier strategies and regular testing to ensure effectiveness. Strengthening vendor relationships through clear SLAs and ongoing communication maximizes value and fosters collaboration.
Continuous employee training is essential for effectively leveraging cloud technologies. Investing in training equips teams with the necessary skills, enhancing both operational efficiency and security posture.
In summary, a multifaceted approach encompassing security, governance, automation, cost management, disaster recovery, vendor collaboration, and employee training is vital for organizations to protect their digital assets and drive innovation in an evolving landscape.




