Introduction
In the ever-evolving landscape of digital security and device management, Microsoft Intune emerges as a pivotal solution for organizations striving to protect their sensitive information while ensuring seamless access for authorized users. This comprehensive cloud-based service offers a suite of features designed to fortify security through Mobile Device Management (MDM) and Mobile Application Management (MAM).
As businesses increasingly adopt remote work models, the need for robust compliance and security measures has never been more critical. This article delves into the core functionalities of Microsoft Intune, best practices for deployment, and strategies for maintaining security and compliance, all while integrating with other Microsoft services to enhance operational efficiency.
By leveraging Intune's capabilities, organizations can navigate the complexities of modern IT environments, ensuring that their devices and applications remain secure and compliant in a rapidly changing technological landscape.
Understanding Microsoft Intune: Core Features and Benefits
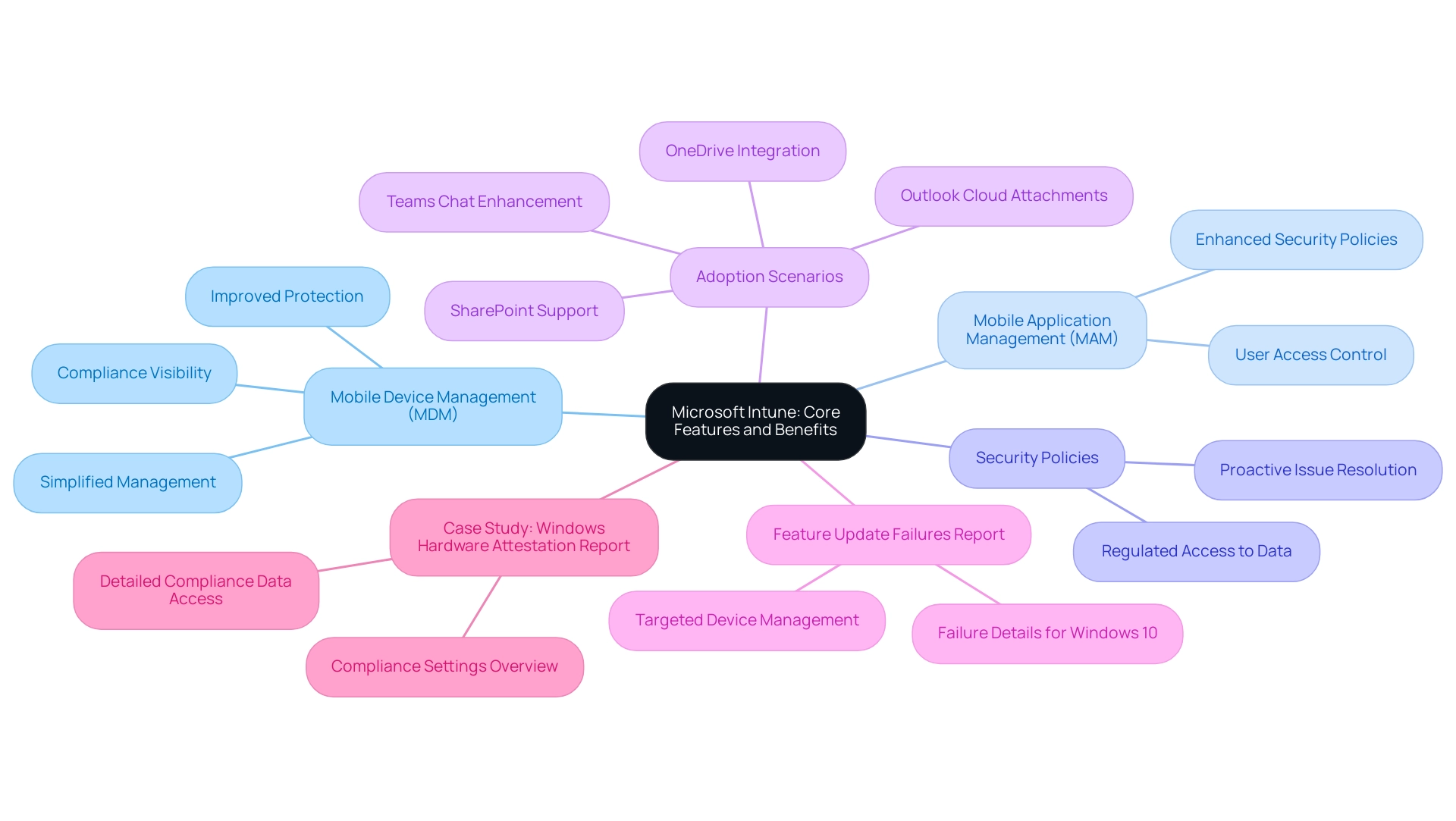
Microsoft's strong cloud-based solution, designed with Microsoft Intune support, enables organizations to oversee and protect their tools and applications efficiently. With essential characteristics like Mobile Device Management (MDM) and Mobile Application Management (MAM), Microsoft Intune support enables IT administrators to implement strict protection policies across multiple platforms. This capability ensures that access to corporate data is tightly regulated, allowing only authorized users to interact with sensitive information.
The advantages of utilizing this system are numerous, including:
- Simplified management of equipment
- Improved protection protocols
- Better adherence to organizational guidelines, all supported by Microsoft Intune support
Supporting a diverse array of devices—spanning Windows, Android, and iOS—Microsoft Intune support proves to be a versatile solution tailored for dynamic IT environments. As highlighted by Scott Sawyer from Microsoft,
We've accomplished a great deal—and enabled some great outcomes for our customers as you'll read below.
This statement highlights the effectiveness of the platform in facilitating secure remote work, particularly significant as businesses prioritize mobile security, with Microsoft Intune support being a crucial factor for 86% of them in response to increased remote operations. Furthermore, the Feature update failures report provides crucial details for IT administrators overseeing updates, ensuring that they can utilize Microsoft Intune support to address issues proactively. The case study titled 'Windows Hardware Attestation Report' illustrates how organizations can utilize Microsoft Intune support to enhance compliance visibility, showcasing the status of hardware-attested settings for enrolled equipment.
Additionally, recent updates that provide Microsoft Intune support enhance adoption scenarios for OneDrive, SharePoint, Teams Chat, and cloud attachments in Outlook, reflecting its relevance in modern IT environments.
Best Practices for Deploying and Configuring Microsoft Intune
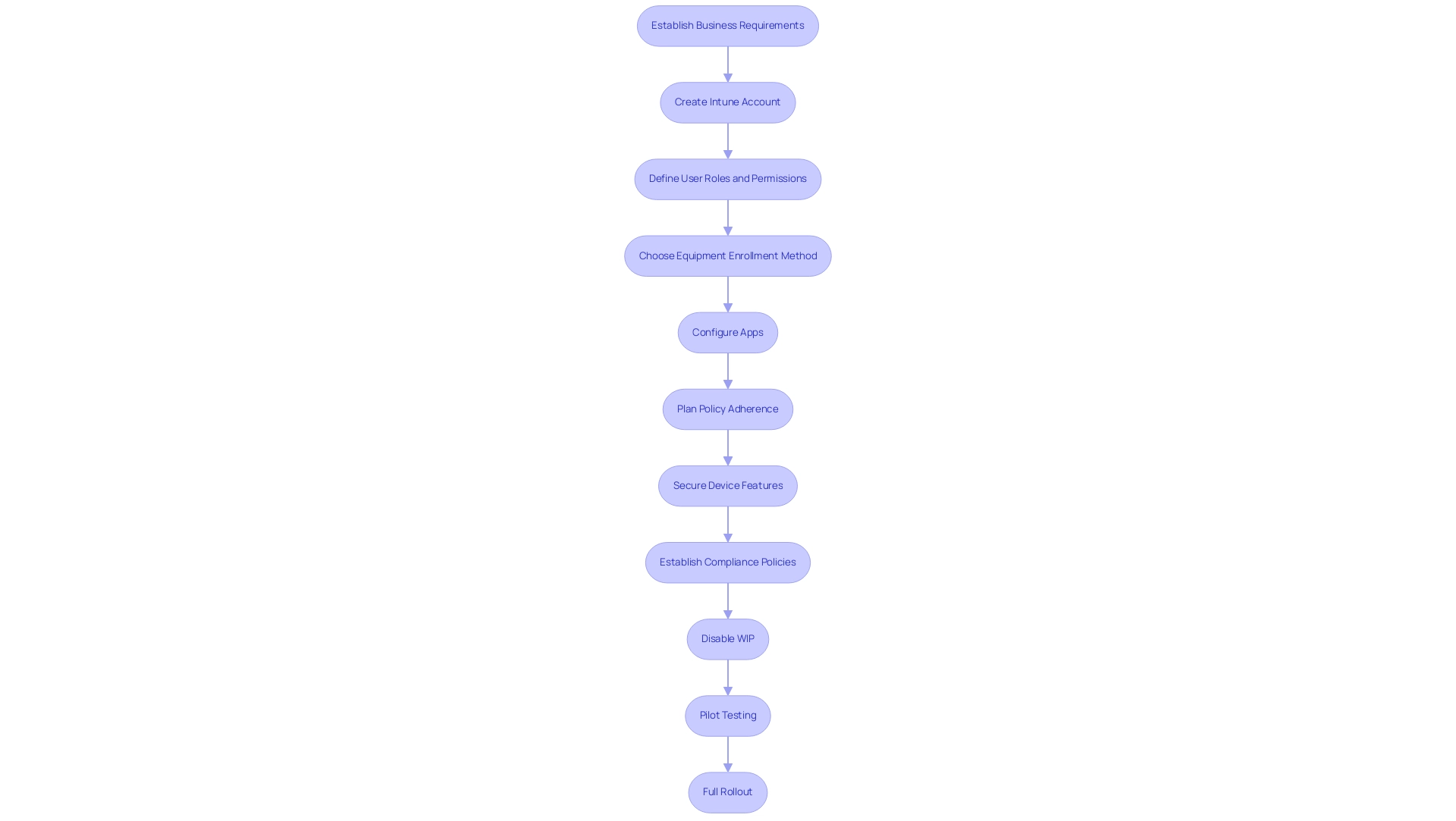
To implement and set up Microsoft management tools effectively, organizations must first establish a clear understanding of their business requirements and the categories of equipment in use. This foundational step ensures that the deployment aligns with organizational goals. The initial setup begins with creating an Intune account, where defining user roles and permissions is critical to maintaining security and operational efficiency.
Organizations should carefully consider their equipment enrollment methods—whether user-driven or automated—based on their unique needs and operational dynamics. Significantly, devices presently registered on MacOS 12. X or lower will stay registered despite the absence of support for those versions, which may affect enrollment strategies.
Next steps in the deployment process involve:
- Configuring apps
- Planning policy adherence
- Securing device features and settings
Establishing compliance policies that align with your organization's protection requirements is crucial. These policies should be regularly reviewed and updated to adapt to evolving security landscapes.
Additionally, organizations are advised to disable Windows Information Protection (WIP) to prevent users from losing access to documents protected by WIP policy, ensuring that data remains accessible and secure.
Testing the configuration through a pilot program before a full rollout can help identify potential issues and facilitate a smoother transition. As emphasized by Hypershift, organizations encountering difficulties in retaining skilled personnel to oversee SCCM may find value in several managed services options that offer continuous support. Microsoft Intune support can prove invaluable in navigating the complexities of system deployment and optimization.
Furthermore, the InstallShield MSI Projects Course exemplifies how training can enhance skills in installation management, which is crucial for effective deployment.
Ensuring Security and Compliance with Microsoft Intune
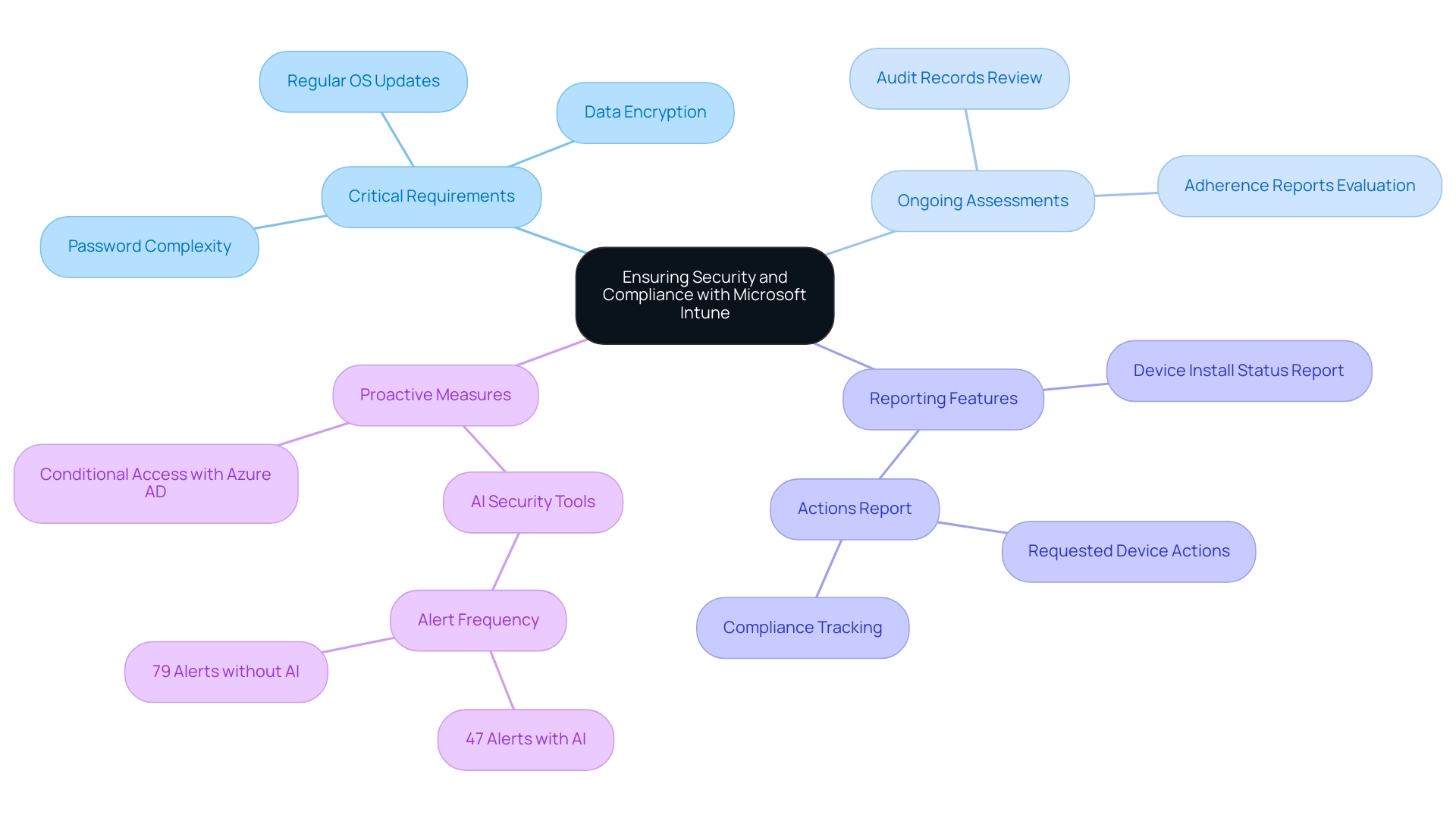
Achieving protection and conformity with Microsoft Intune support necessitates the development of comprehensive safety configurations and ongoing assessments of adherence status. Organizations are encouraged to establish regulations that enforce critical requirements, including:
- Password complexity
- Data encryption
- Regular operating system updates
Frequent evaluations of audit records and adherence reports are crucial for identifying possible vulnerabilities and tackling non-adherence matters proactively.
Significantly, the powerful reporting features of the platform enable IT teams to oversee adherence across all devices efficiently and take required measures when inconsistencies occur. According to a statistic on AI protection tools, organizations using these solutions receive an average of 47 alerts per day, compared to 79 alerts among those not using AI solutions, highlighting the effectiveness of proactive protective measures. Moreover, Microsoft Intune support, when merged with Azure Active Directory, greatly enhances protective measures by allowing conditional access according to adherence status.
Omdia has acknowledged Microsoft as a leader in the Omdia Universe for Digital Workspace Management, reinforcing the platform's reliability and the importance of Microsoft Intune support in upholding safety standards. Additionally, the Actions Report provides essential information for compliance tracking and streamlining audit processes, helping organizations maintain compliance by tracking action statuses. By utilizing these tools and strategies, organizations can safeguard their digital environments while meeting regulatory obligations and enhancing operational efficiency.
Integrating Microsoft Intune with Other Microsoft Services
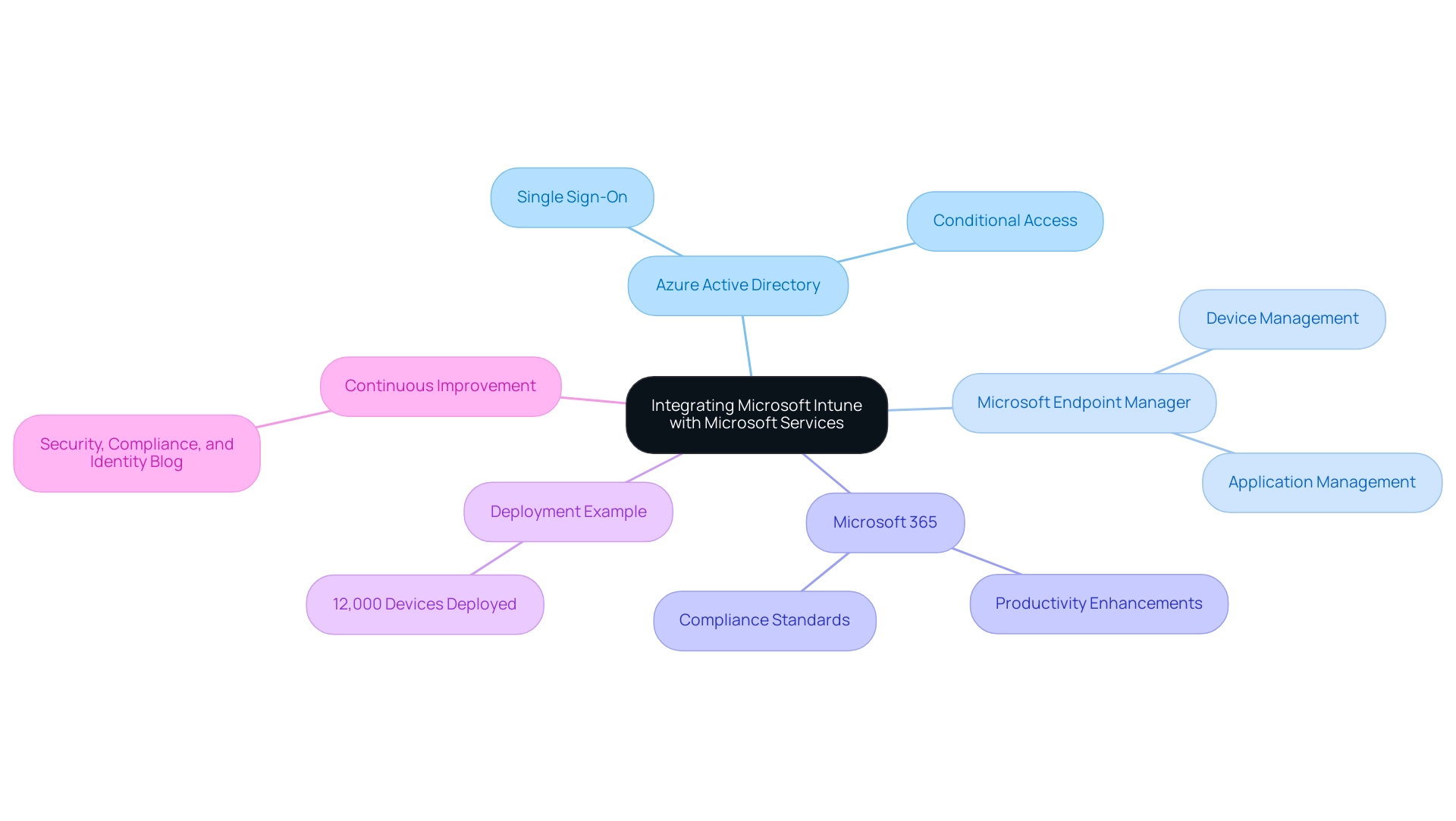
Combining Microsoft Intune support with vital Microsoft services like Azure Active Directory, Microsoft Endpoint Manager, and Microsoft 365 can significantly improve an organization's management and protection capabilities. By utilizing Azure Active Directory for identity management, organizations can facilitate seamless single sign-on experiences and enforce strong conditional access policies, which are essential for preserving security across platforms. The integration of Microsoft Endpoint Manager and Microsoft Intune support further streamlines the management of both devices and applications, ensuring that IT teams can deploy and update resources efficiently across the organization.
This collaboration fosters enhanced productivity, allowing teams to access applications and data securely while adhering to compliance standards. Regularly reviewing these integration points is vital to ensure alignment with evolving business objectives and security requirements. Significantly, a successful deployment example includes Pradeep Saxena, who effectively managed the deployment of 12,000 devices using Microsoft technology, showcasing the scalability and effectiveness of this integration in a real-world context.
Additionally, Bjarne Mattila emphasizes that 'in Sophos you will have disk encryption, AV, Intercept-X (best anti ransomware on the market), EDR, Enhanced EDR, Synchronized Security via Security Heartbeat and ZTNA for both Endpoints and Smart Phones, supports O365 and has integration into Microsoft management system.' He further notes that these solutions are 'logical and easy to setup, maintain, support and costs much less than other options,' advocating for the strategic adoption of these technologies. For ongoing updates and insights, users can follow the Security, Compliance, and Identity Blog.
Navigating Support and Troubleshooting for Microsoft Intune
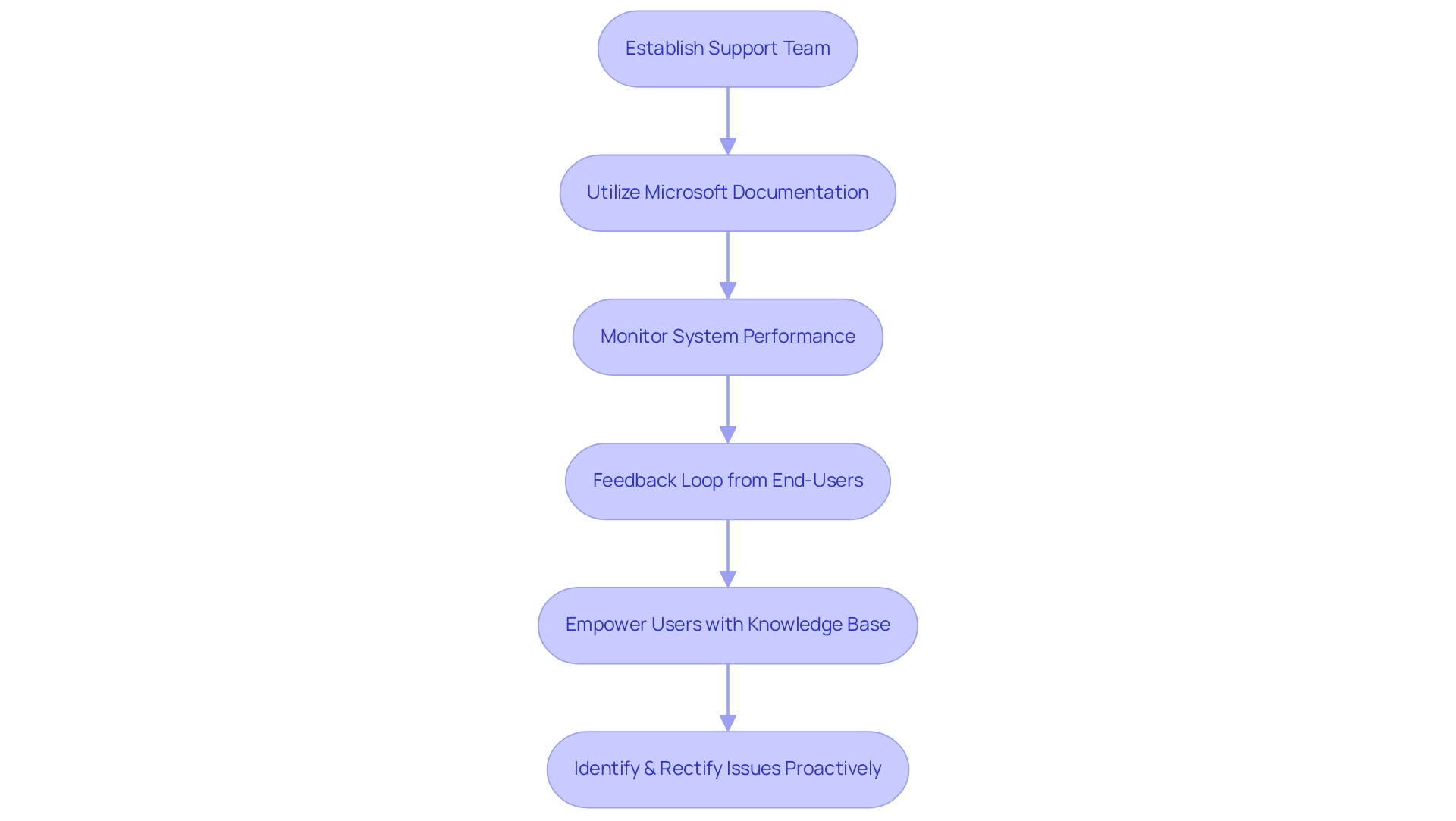
Establishing an effective support structure for Microsoft Intune support is crucial for organizations aiming to streamline their troubleshooting processes. A dedicated support team, well-versed in the platform's functionalities, is essential for addressing issues efficiently. This team should leverage Microsoft's comprehensive documentation and community forums, which serve as invaluable resources for resolving common problems.
For instance, the Windows Hardware Attestation Report, available through the Microsoft admin center, allows users to view compliance settings and ensure systems conform to organizational policies. Additionally, the Feature update failures report provides critical failure details for devices targeted with Feature updates, highlighting the importance of monitoring these updates as part of the support structure. Empowering users with a regularly updated knowledge base can foster independent problem-solving for minor issues.
Proactive monitoring tools are also beneficial, allowing IT teams to identify and rectify potential problems before they disrupt user experience. Furthermore, establishing a feedback loop from end-users can significantly enhance the support process, ensuring that user concerns are addressed promptly. As noted by IT professional Erland Sommarskog:
- "Seems that you are not very keen on getting help, since you are not sharing much information... effective communication and data sharing are paramount to improving troubleshooting outcomes."
This emphasizes that a structured approach is not just beneficial but essential for maximizing the capabilities offered by Microsoft Intune support. Moreover, considering that the CPU usage of the process 'svchost' can reach up to 43, monitoring system performance is also vital for troubleshooting efficiency.
Conclusion
In summary, Microsoft Intune stands out as an essential tool for organizations aiming to enhance their digital security and device management strategies. Its core features, including Mobile Device Management (MDM) and Mobile Application Management (MAM), provide a comprehensive framework for enforcing security policies and ensuring compliance across diverse device environments. By adopting best practices for deployment and configuration, organizations can tailor Intune to align with their unique operational needs, thus optimizing security while facilitating efficient device management.
Moreover, maintaining robust security and compliance through Intune involves the establishment of rigorous policies and regular audits. The integration of Intune with other Microsoft services, such as Azure Active Directory and Microsoft 365, further amplifies its capabilities, enabling seamless access and enhanced productivity. These integrations not only streamline management but also bolster security measures, ensuring that organizations can navigate the complexities of modern IT landscapes with confidence.
Finally, effective support and troubleshooting mechanisms are vital for maximizing the potential of Microsoft Intune. By leveraging available resources and fostering clear communication within support teams, organizations can address challenges proactively, ensuring that their security framework remains robust and responsive. Embracing Microsoft Intune is not merely a strategic choice; it is a critical step toward safeguarding sensitive information and enhancing operational efficiency in an increasingly digital world.




