Introduction
In the rapidly evolving landscape of technology, effective network deployment services have become a cornerstone for organizations striving to maintain a competitive edge. This comprehensive guide delves into the essential processes and best practices for establishing and managing robust network infrastructures. From the critical phases of assessment and planning to the intricacies of implementation and ongoing maintenance, understanding these key concepts is paramount.
With an emphasis on security, configuration management, and continuous optimization, this article equips enterprise IT leaders with the knowledge needed to navigate the complexities of network deployment. By adhering to proven strategies and embracing innovative solutions, organizations can ensure their networks not only meet current demands but are also poised for future growth.
Understanding Network Deployment Services: Key Concepts and Processes
Network deployment services encompass a comprehensive suite of processes aimed at establishing and managing infrastructure with precision. Understanding key concepts is essential for effective implementation:
- Assessment and Planning: This foundational phase involves a thorough analysis of the existing infrastructure landscape, pinpointing business requirements, and comprehending user demands.
This critical evaluation informs the design of a new system that aligns with organizational objectives. As enterprise IT leaders prepare for substantial investments in next-gen hardware infrastructure and management of safety, these factors play a vital role in shaping the design and architecture.
- Design and Architecture: Following the assessment, a detailed infrastructure design is crafted, encapsulating the architecture, technology stack, and configurations necessary to fulfill the identified objectives.
Key factors during this phase involve scalability and adaptability, ensuring the system can adjust to changing business requirements.
- Execution: During this phase, the actual deployment of hardware and software components occurs, encompassing routers, switches, firewalls, and management systems. A notable trend in this area is the adoption of private wireless small cells, which serve as a cost-effective alternative to Distributed Antenna Systems (DAS) for providing improved connectivity in both enterprise and public venues.
Effective coordination among various teams is paramount to guarantee a seamless rollout of network deployment services, minimizing disruptions to ongoing operations.
-
Testing and Validation: After deployment, thorough testing is crucial to ensure that the system complies with set standards for efficiency and protection. This may include stress testing, benchmarking efficiency, and thorough protection evaluations to confirm the system's robustness.
-
Monitoring and Maintenance: Continuous monitoring post-deployment is critical to ensure optimal performance and security. This includes regular updates, troubleshooting procedures, and adjustments tailored to accommodate shifting business requirements. According to a recent survey, 48% of respondents identified lifecycle management as the foremost feature of Network as a Service (NaaS) providers, underscoring the importance of ongoing management in infrastructure.
As enterprise IT leaders navigate these implementation processes, understanding the interplay between investment strategies and design becomes crucial, particularly in light of the recent trends and case studies shaping the future of infrastructure implementation.
Expert Tips for Successful Network Deployment Implementation
For a successful network deployment, consider the following expert recommendations:
-
Engage Stakeholders Early: Involving key stakeholders from the outset is essential. This not only aids in collecting various perspectives but also fosters a cooperative environment, ensuring that the implementation aligns with overarching business goals and user needs. Research indicates that transformations are four times more likely to succeed when influential employees are engaged—emphasizing their crucial role in this process. As highlighted by the case study "Network Motifs in Stakeholder Engagement," understanding the structural characteristics of stakeholder interactions can provide valuable insights into how to effectively engage these individuals.
-
Develop a Comprehensive Project Plan: A well-structured project plan is vital. It should delineate timelines, responsibilities, and key milestones, while also incorporating risk management strategies to preemptively address potential challenges. This is particularly important as stakeholder dynamics can vary significantly across public, private, and PPP projects, with a maximum density value of 1 indicating the potential for complex interactions among stakeholders, as revealed in recent analyses of network motifs in stakeholder engagement.
-
Prioritize Security from the Start: Security must be a foundational element of the implementation strategy. This involves configuring firewalls, establishing access controls, and ensuring compliance with relevant industry standards from the beginning.
-
Invest in Training: Adequate training for both IT staff and end-users is paramount to ensure familiarity with new systems. This commitment to training not only boosts user adoption rates but also minimizes operational disruptions during the transition.
-
Implement a Phased Rollout: A phased implementation approach allows for the gradual integration of new systems, enabling organizations to identify and resolve issues early in the process. This strategy significantly reduces the potential impact on ongoing business operations.
-
Monitor Performance Continuously: After the implementation is complete, it is essential to use monitoring tools to consistently evaluate performance metrics and collect user feedback. This proactive approach facilitates the swift identification of issues and supports ongoing enhancements to services.
In summary, as Taylor Lauricella recommends, involving influential employees is vital for successful change—organizations should prioritize their participation to improve the chances of a successful network deployment services.
Best Practices for Network Configuration Management
Effective configuration management is crucial for ensuring the reliability and security of modern IT environments. Here are several best practices that should be considered for 2024:
-
Maintain an Up-to-Date Configuration Inventory: It is essential to keep a comprehensive inventory of all devices and their configurations.
This meticulous tracking aids in quick recovery during incidents and ensures that configurations are aligned with business needs. As noted in industry reports, accounting management measures utilization parameters for individual or group users, highlighting the necessity of accurate configuration data to optimize resource allocation and enhance overall performance. -
Utilize Automated Tools: The implementation of automated configuration management tools significantly enhances efficiency and consistency across device systems.
These tools minimize human error and free up valuable time for IT teams, allowing them to focus on strategic initiatives rather than manual management. The shift towards automation has become a critical component in maintaining effective system management. -
Regularly Review and Audit Configurations: Routine assessments of system configurations are essential to ensure adherence to organizational standards and to identify possible weaknesses.
Regular reviews not only enhance security but also align configurations with evolving business requirements. -
Version Control for Configurations: Utilizing version control systems for configurations is essential.
This practice allows organizations to track changes effectively and revert to previous versions if necessary. Keeping a record of configuration changes aids in troubleshooting and root cause analysis, especially when syslog messages from routers and switches point out issues, thus improving the overall reliability of operations. -
Establish Change Management Procedures: Creating formal procedures for configuration changes is imperative.
Comprehensive documentation, review, and approval processes reduce risks linked to modifications, ensuring that changes do not unintentionally disturb operations. Cem Dilmegani, a principal analyst at AIMultiple, emphasizes the strategic importance of such structured approaches in optimizing system performance, asserting that well-defined change management processes are key to sustaining operational excellence.
Incorporating these best practices not only enhances the management of complex IT environments but also aligns with the latest industry trends, such as the proactive monitoring capabilities enabled by RMON.
By setting thresholds that alert SNMP platforms when issues arise, organizations can shift towards a more proactive operational model, as evidenced by successful implementations of ITIL Configuration Management, which lead to improved disaster prevention and faster troubleshooting.
Ensuring Network Security During Deployment
Integrating strong security protocols during system installation is crucial for reducing risks and protecting sensitive information. The following best practices should be prioritized:
- Perform a Risk Evaluation: Prior to implementation, a thorough risk evaluation must be carried out to identify possible weaknesses within the system.
This proactive approach allows organizations to devise targeted strategies for mitigating identified risks, ensuring a secure environment for network deployment services.
-
Use Secure Protocols: It is crucial to utilize secure communication protocols, such as SSH and HTTPS, for device configuration and management. With 92% of malware being delivered via email, these protocols help protect data in transit, reducing the likelihood of interception by malicious actors.
-
Implement Strong Access Controls: Establishing role-based access controls (RBAC) is essential for managing who can make modifications to devices. By ensuring that only authorized personnel have the ability to alter configurations, organizations can significantly decrease the risk of unauthorized access.
-
Segment the Network: Implementing network segmentation is another effective strategy. By restricting the blast radius of potential breaches, segmentation makes it more challenging for attackers to access critical systems, thereby enhancing overall resilience.
-
Regular Protection Training: Ongoing education for IT personnel on the latest protective practices and emerging threats is imperative. Regular training sessions on network deployment services promote a security-first mindset, equipping teams with the knowledge necessary to effectively navigate the challenges of implementation.
The stakes are high; statistics indicate that 60% of small businesses that suffer a cyber attack go out of business within six months. Furthermore, the number of known spear-phishing groups has increased from 116 in 2016 to over 250 in 2018, highlighting the growing threat landscape. Additionally, the average total cost of a mega breach, involving 50 to 60 million records, can soar to $332 million.
A notable example of the consequences of inadequate security measures is the Target data breach in 2013, where malware was used to steal data from point of sale systems, compromising the information of approximately 110 million credit/debit card holders. These concerning statistics demonstrate the disastrous financial repercussions that can result from large-scale data breaches, emphasizing the significance of applying these best practices during system setup.
Post-Deployment Evaluation and Optimization
After the implementation of a system, organizations must prioritize ongoing assessment and enhancement to ensure sustained effectiveness and reliability. Here are key steps to implement this effectively:
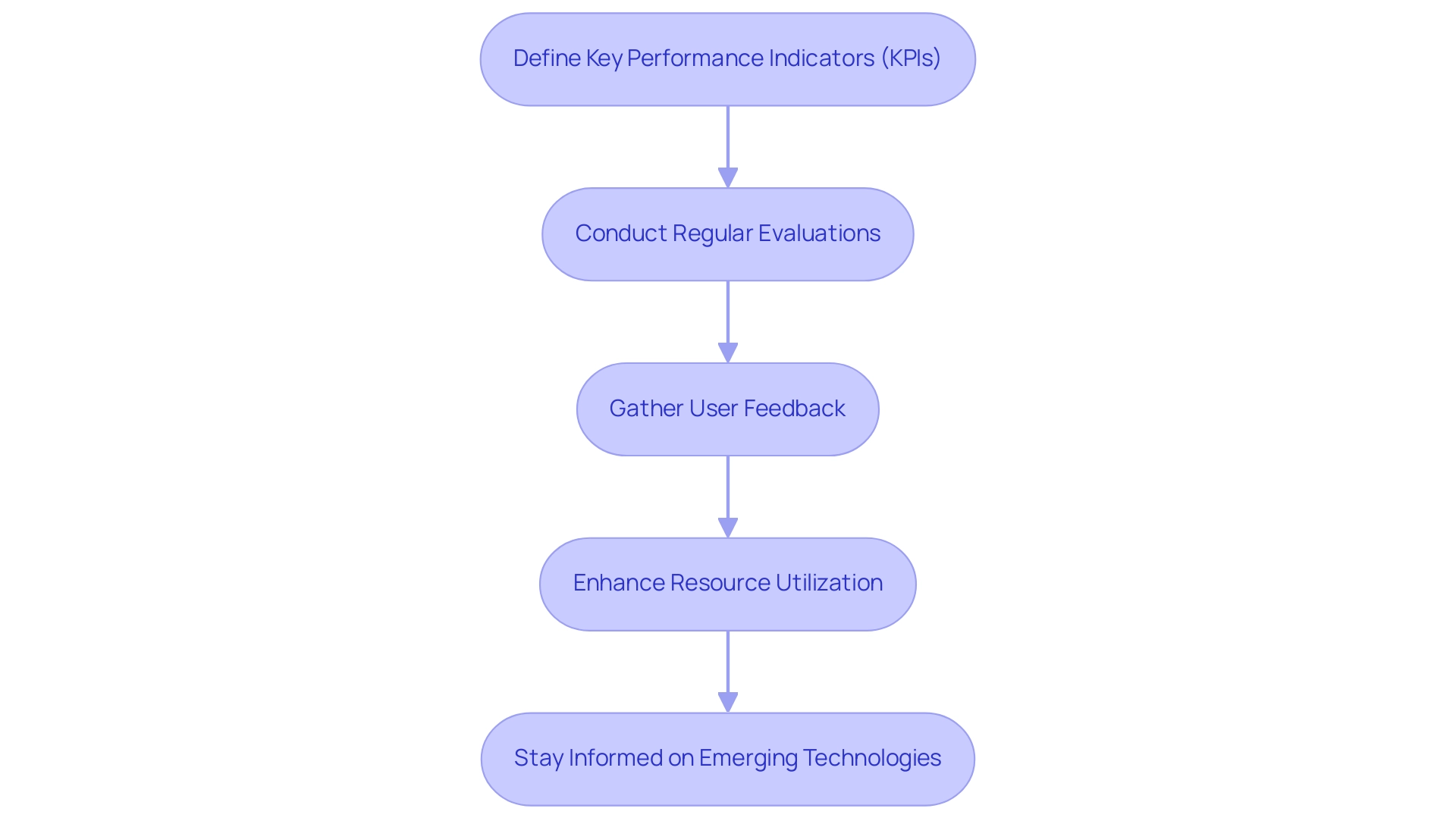
- Define Key Performance Indicators (KPIs): Establishing strong KPIs is crucial for assessing system effectiveness.
Key metrics such as uptime, latency, and throughput serve as benchmarks that help organizations assess the effectiveness of their infrastructure. According to industry insights, a well-defined KPI framework not only aids in tracking results but also highlights areas requiring immediate attention. For instance, understanding the phishing attack success rate underscores the critical need for user training and awareness in enhancing network security.
- Conduct Regular Evaluations: Establishing a routine for assessments against these KPIs is critical.
Regular assessments allow for the identification of bottlenecks and inefficiencies, facilitating timely interventions. An effective approach to performance evaluation is to utilize the Mean Time to Detect (MTTD) as a KPI, which measures the responsiveness of cybersecurity measures.
This KPI is vital for evaluating the effectiveness of an organization's cybersecurity strategies and can significantly improve overall system security.
- Gather User Feedback: Actively collecting feedback from end-users is vital for understanding their experiences with the system.
User insights can identify specific issues and emphasize areas for enhancement, ensuring that the system aligns with operational needs.
As Ben Cone, a Senior Solutions Engineer at INOC, emphasizes,
Understanding user interaction is essential; it reveals training needs and potential vulnerabilities in system security.
This insight reinforces the importance of user feedback in optimizing system performance.
- Enhance Resource Utilization: Leveraging information from evaluations and user input allows organizations to make informed modifications to resource allocation.
This includes optimizing bandwidth allocation and refining routing configurations to enhance overall efficiency and performance.
- Stay Informed on Emerging Technologies: The environment of connectivity efficiency is rapidly evolving, making it essential for organizations to stay updated on emerging technologies.
Ongoing observation of industry trends can offer insights into innovative solutions that improve system functionality, security, and efficiency.
Integrating these advancements into the network strategy through network deployment services can yield significant competitive advantages.
By implementing these best practices and utilizing relevant KPIs such as MTTD, organizations can ensure that their networks remain robust and responsive, ultimately driving better performance and user satisfaction.
Conclusion
Establishing and managing a robust network infrastructure is vital for organizations aiming to thrive in today's technology-driven environment. The comprehensive guide outlined essential processes, from assessment and planning to implementation and ongoing maintenance, underscoring the significance of each phase in ensuring effective network deployment. By engaging stakeholders early and developing a structured project plan, organizations can align their network deployment with business objectives while prioritizing security from the outset.
Furthermore, the article emphasized best practices in network configuration management and the critical need for continuous monitoring and optimization post-deployment. Employing automated tools and maintaining an up-to-date configuration inventory are key strategies that enhance operational efficiency and security. The importance of conducting risk assessments and implementing strong access controls cannot be overstated, as these practices mitigate vulnerabilities and protect sensitive data.
Ultimately, a proactive approach to network deployment and management not only addresses current demands but also positions organizations for future growth. By embracing innovative solutions and adhering to proven strategies, enterprise IT leaders can navigate the complexities of network deployment with confidence, ensuring their infrastructures are resilient, secure, and optimized for success.




