Introduction
In the rapidly evolving landscape of information technology, organizations are increasingly turning to innovative strategies to enhance their IT infrastructure. This article explores a multifaceted approach, highlighting the integration of artificial intelligence to streamline operations, the implementation of robust data privacy practices, and the optimization of infrastructure for scalability. Furthermore, it delves into the critical importance of enhancing cybersecurity measures and fostering a culture of continuous improvement within teams.
By examining these key areas, organizations can not only bolster their operational efficiency but also safeguard sensitive information and adapt to the ever-changing demands of the digital era.
Harnessing AI for Enhanced IT Infrastructure Performance
To harness AI effectively within IT infrastructure, organizations should start by identifying key areas where automation and analytics can enhance efficiency. Implementing AI-driven monitoring tools can help predict system failures before they occur, minimizing downtime and improving service availability. For instance, utilizing machine learning algorithms to analyze historical performance information can lead to proactive maintenance schedules.
Additionally, AI chatbots can streamline IT support, providing users with instant assistance and freeing up IT staff for more complex tasks.
It's essential to foster a culture of innovation by encouraging teams to explore AI applications that align with business objectives, thereby turning AI into a strategic asset rather than just a technological upgrade.
Implementing Data Privacy Best Practices in IT Infrastructure
Implementing privacy best practices begins with a thorough audit of management processes. This audit should concentrate on categorizing information by sensitivity and instituting stringent access controls to ensure that only authorized personnel can access sensitive information. The importance of these measures is underscored by the fact that 55% of companies still lack even basic email security training, leaving employees vulnerable to common threats. Case studies emphasize the critical nature of this training, demonstrating that negligence can result in significant breaches.
As noted by privacy expert Jane Doe, "Regular audits and robust access controls are not just best practices; they are essential for protecting sensitive information in today's digital landscape." Advanced encryption technologies for information at rest and in transit are vital for maintaining integrity. Regular training sessions on privacy policies should be ingrained in the organizational culture, as human error is a leading cause of breaches. Expert opinion reinforces this, noting that consistent training can drastically reduce the risk of breaches.
Recent news emphasizes that companies such as ABC Corp have effectively established robust access controls, leading to a 40% decrease in breaches over the past year. Recent developments in encryption technologies further bolster these efforts, providing more robust protection against unauthorized access. Additionally, having a clear and actionable incident response plan is essential. This ensures that any potential breaches are addressed swiftly and effectively, minimizing damage and ensuring compliance with regulatory requirements. By integrating these practices, entities can significantly enhance their data privacy posture.
Optimizing IT Infrastructure for Scalability
To optimize IT infrastructure for scalability, entities should adopt cloud solutions that allow for on-demand resource allocation. Leveraging Infrastructure as a Service (IaaS) enables businesses to scale their IT resources up or down based on current needs, facilitating cost-effectiveness.
Implementing containerization technologies can also enhance scalability by allowing applications to run consistently across various environments. Regularly reviewing and assessing the performance of IT systems is critical to identifying areas that may become bottlenecks as demand increases.
Furthermore, organizations should consider adopting a microservices architecture to improve flexibility and facilitate independent scaling of different components of their applications.
Enhancing Cybersecurity Measures in IT Infrastructure
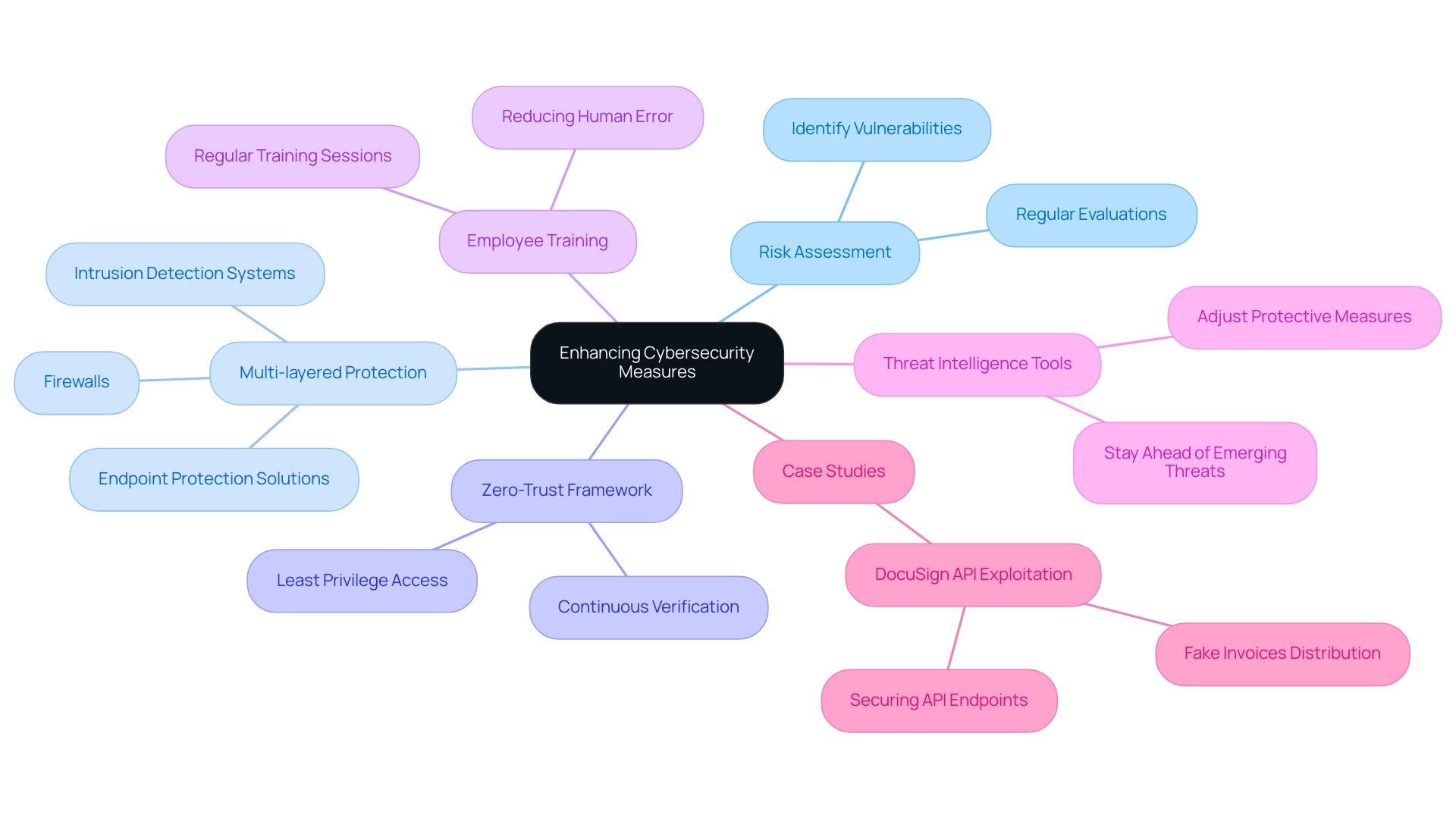
Enhancing cybersecurity measures necessitates a thorough risk assessment to identify vulnerabilities within the IT infrastructure. A multi-layered protective approach is essential for safeguarding critical assets against a wide range of cyber threats. This involves deploying:
- Firewalls
- Intrusion detection systems
- Endpoint protection solutions
Regularly updating software and systems to patch known vulnerabilities is crucial in preventing attacks. Recent findings emphasize that 65% of websites remain unprotected from bots, underscoring the need for strong protection protocols. As cybersecurity specialist Dr. Emily Chen indicates, 'Organizations must prioritize regular risk evaluations to understand their unique vulnerabilities and adjust their protective measures accordingly.'
Adopting a zero-trust framework ensures that no entity, whether internal or external, is trusted by default. Recent trends indicate that more organizations are implementing zero-trust frameworks to enhance their defenses, emphasizing continuous verification and least privilege access. Regina Lester, Vice President of Safety & Protection Operations at Toledo Zoo, emphasizes, 'In this webinar, I will share insights on implementing safety technologies in the entertainment sector and balancing budget constraints with safety needs.'
A practical example can be seen in the recent report on malicious actors exploiting DocuSign's APIs to distribute fake invoices. This case study stresses the importance of securing API endpoints against exploitation. Regular training for employees is also essential in reducing risks linked to human error. Employing threat intelligence tools enables organizations to stay ahead of emerging threats and adjust their protective measures accordingly.
Ultimately, the effectiveness of a multi-layered defense approach lies in its comprehensive nature, addressing various aspects of cybersecurity to create a resilient IT infrastructure. The stark statistic that 65% of websites are unprotected from bots highlights the critical need for such an approach, as it can significantly reduce vulnerabilities and enhance overall security posture.
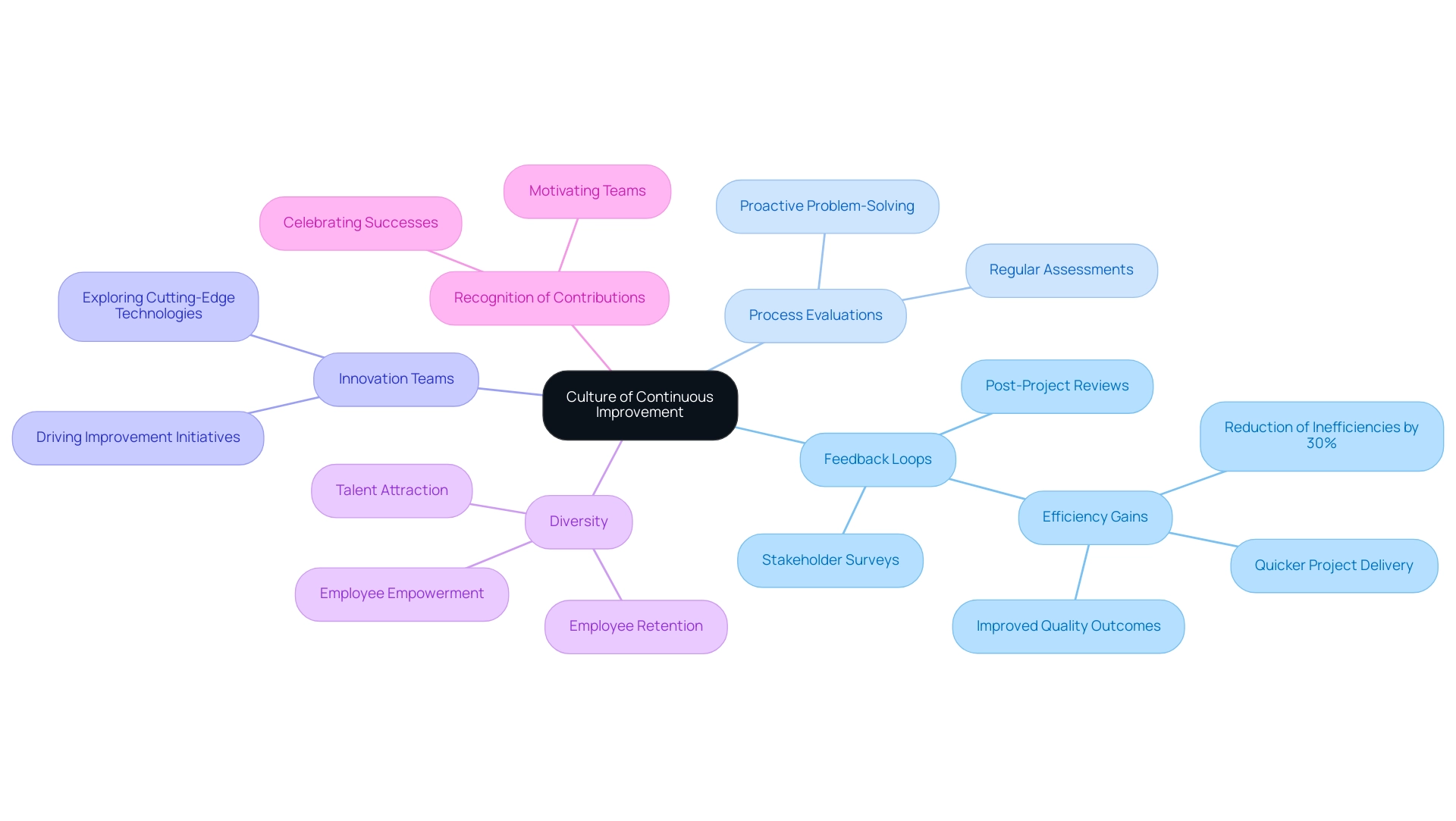
Fostering a Culture of Continuous Improvement
Fostering a culture of continuous improvement is pivotal for enhancing IT infrastructure management. Encouraging teams to regularly assess workflows through feedback loops, such as post-project reviews and stakeholder surveys, significantly identifies areas for enhancement and directly impacts efficiency. Research indicates that organizations employing feedback loops can diminish inefficiencies by up to 30%, resulting in quicker project delivery and improved quality outcomes. According to Donielle Boudin, Director of Quality, 'At a moment’s notice, we can see the pulse of where our quality system lies. My management review procedure has gone from five days of data crunching and analyzing graphs and spreadsheets to a 5-minute report and I’m done,' highlighting the efficiency gains from streamlined methods.
In addition, leaders like [Insert Leader's Name and Position] emphasize that regular process evaluations foster a proactive approach to problem-solving, which is essential for continuous improvement. Implementing strategies such as forming dedicated innovation teams can drive initiatives that explore cutting-edge technologies and methodologies. Promoting a mindset of learning and adaptation empowers employees to propose and experiment with new ideas, which is crucial for maintaining a competitive edge. For instance, diverse workplaces are shown to be more attractive to potential employees and improve retention, emphasizing the role of diversity in fostering a culture of continuous improvement. Celebrating successes and recognizing contributions to improvement initiatives further motivate teams to actively engage in this culture, ultimately leading to greater overall effectiveness in IT infrastructure management.
Conclusion
Integrating artificial intelligence into IT infrastructure presents a vital opportunity for organizations to enhance operational efficiency. By employing AI-driven tools for predictive maintenance and streamlined support, businesses can significantly reduce downtime and foster innovation aligned with strategic objectives.
Robust data privacy practices are essential for safeguarding sensitive information. Conducting thorough audits, enforcing strict access controls, and providing regular training can markedly reduce the risk of data breaches, as evidenced by successful case studies.
Scalability is critical, with cloud solutions and containerization technologies enabling organizations to adapt swiftly to changing demands. Regular performance assessments identify potential bottlenecks, ensuring seamless growth.
Enhancing cybersecurity through a multi-layered approach is crucial for protecting valuable assets. Implementing a zero-trust security model and prioritizing employee training fortifies defenses against diverse threats.
Finally, fostering a culture of continuous improvement is key to driving efficiency and innovation. Encouraging feedback loops and proactive problem-solving empowers teams to respond effectively to rapid technological advancements.
In summary, organizations that embrace these interrelated strategies—leveraging AI, prioritizing data privacy, optimizing scalability, enhancing cybersecurity, and nurturing continuous improvement—can build a robust and agile IT infrastructure. This holistic approach not only boosts operational efficiency but also strengthens defenses against emerging threats, positioning businesses for sustained success in a complex digital landscape.




