Introduction
In the digital age, a comprehensive antivirus solution is paramount for safeguarding sensitive information and maintaining robust cybersecurity. This article delves into the core components that constitute an effective antivirus solution, from real-time protection to heuristic analysis, and the importance of an extensive malware database. It further explores best practices for configuring antivirus solutions, emphasizing the significance of tailored settings, scheduled scans, and alert configurations to maximize security.
Advanced threat detection techniques, including behavioral analytics and machine learning, are highlighted for their role in preemptively identifying potential threats. Additionally, the critical practice of automating patch management and security updates is examined, illustrating how it minimizes vulnerabilities and enhances overall security posture. Finally, the necessity of conducting regular security audits and continuous employee training is underscored to ensure the efficacy of antivirus measures and foster a culture of cybersecurity awareness.
Core Components of an Effective Antivirus Solution
An effective antivirus solution should integrate several critical components, including real-time protection, heuristic analysis, and a robust malware database. Real-time protection actively scans files as they are accessed, ensuring immediate detection and response to dangers. This ability is crucial for sustaining a proactive defense against cyber dangers. Heuristic analysis, conversely, enables the method to identify new, previously unknown viruses by examining code behaviors. This method is essential for identifying zero-day vulnerabilities that traditional signature-based systems might overlook.
A thorough malware database guarantees that the antivirus program can identify and protect against a broad range of dangers. This database should be regularly updated to include the latest danger signatures. Furthermore, incorporating cloud-based risk intelligence can greatly improve the solution's capacity to address emerging challenges. Cloud integration enables the exchange of risk information across various systems, offering a wider and more current view on potential dangers.
According to a recent report, the risk landscape is continually evolving, with geopolitical events influencing the tactics and approaches of many malicious actors. For instance, the 2023 Cisco Talos Year in Review highlights the evolution of ransomware and the increasing rate of attacks against network infrastructure devices. Such insights emphasize the significance of possessing a dynamic and comprehensive antivirus solution capable of adapting to new and advanced dangers.
Furthermore, as pointed out by cybersecurity specialists, the importance of danger intelligence cannot be overstated. By understanding the Tactics, Techniques, and Procedures (TTPs) of threat actors, organizations can make more informed decisions about their cybersecurity strategies. Incorporating this intelligence into security measures guarantees a proactive strategy, efficiently reducing possible attacks before they happen.
Best Practices for Configuring Antivirus Solutions
Effective configuration is crucial for maximizing the potential of antivirus solutions. Administrators should start by reviewing and adjusting default settings to match the organization’s specific security policies. This involves setting appropriate sensitivity levels for danger detection and enabling scheduled scans to ensure ongoing protection. According to a comprehensive study by the Technology Alliance Partner (TAP) Program, organizations only prevent 6 out of every 10 attacks. This highlights the importance of fine-tuning antivirus configurations to bolster preventive measures while maintaining robust detection capabilities.
Additionally, configuring alerts and notifications is essential for prompt threat response. Ensuring compatibility with other existing protective measures is vital for a cohesive defense strategy. The TAP Program study also revealed that healthcare organizations, despite being the least effective at preventing attacks, are twice as successful as the average organization in detecting them. This underscores the need for a balanced approach in antivirus configuration to achieve both preventive and detective efficiency.
Utilizing Advanced Threat Detection Techniques
To enhance endpoint security, organizations should adopt advanced risk detection techniques like behavioral analytics and machine learning algorithms. These technologies can identify unusual patterns in user behavior and system processes, allowing for the early detection of potential risks. Leveraging unique datasets, organizations can tailor these models to their specific needs, while also adhering to compliance standards and legal requirements. For instance, the SANS Faculty has been pioneering the use of AI and ML in cybersecurity, providing insights and practical solutions to stay ahead of evolving challenges.
Establishing sandboxing environments provides an additional level of protection, allowing the safe examination of questionable files without jeopardizing system integrity. This method is crucial, as modern applications often involve complex, internet-connected IT systems interfacing with critical OT systems, and a variety of cloud providers and protocols. Regular updates to detection algorithms and danger signatures are essential to keep pace with the dynamic cyber risk landscape. As stated in the Microsoft Digital Defense Report, large volumes of information are necessary to remain proactive against risks, highlighting the significance of ongoing advancement and innovation in protective measures.
To further illustrate, ProKYC, a sophisticated malicious entity targeting financial institutions, highlights the need for continuous advancements in detection and prevention techniques. By employing multi-factor authentication (MFA) and other strong protective measures, organizations can significantly reduce risks. As OPSWAT CEO Benny Czarny highlights, a thorough strategy is essential to stop malware risks, particularly in the constantly changing environment of protection. Guaranteeing the safety of file uploads and other essential operations is crucial as the threat vector increases and the attack surface widens.
Automating Patch Management and Security Updates
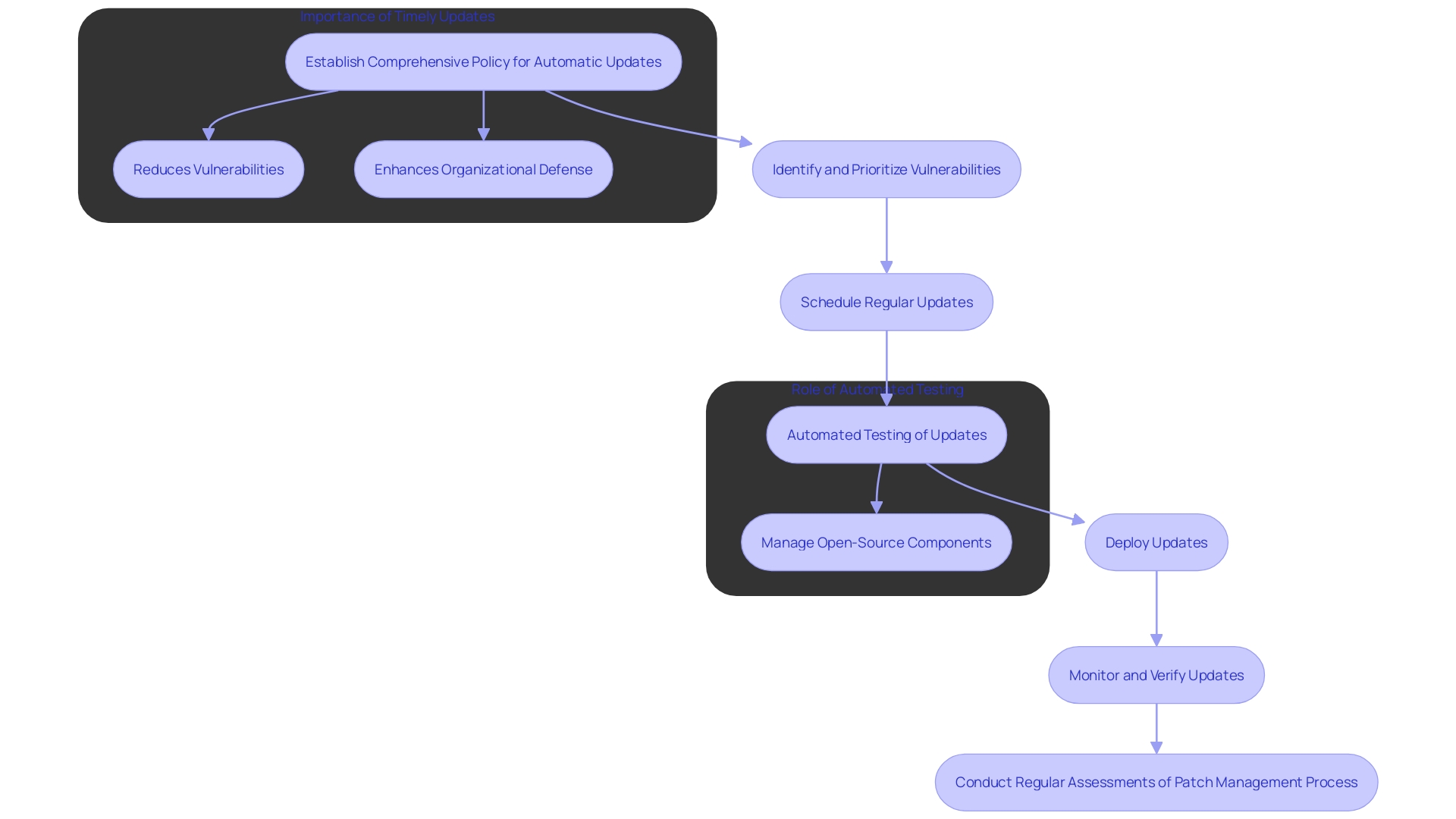
Automating patch management serves as an essential best practice for ensuring that antivirus solutions and other software consistently receive the latest updates and definitions. This not only reduces the window of vulnerability that cybercriminals can exploit but also strengthens the organization's overall defense posture. Organizations should establish a comprehensive policy for automatic updates, paired with regular assessments of the patch management process to ensure compliance and functionality. As pointed out by industry specialists, software updates play a crucial role in addressing vulnerabilities, with cybercriminals constantly looking for weaknesses to exploit.
For instance, Delivery Hero, a global leader in local delivery, faced significant challenges with employees getting locked out of their accounts, impacting productivity. By implementing a robust endpoint management solution, they streamlined the process, reducing downtime and improving overall safety. Similarly, the importance of maintaining optimal conditions for end-user equipment and ensuring timely updates is underscored by the experience of Moreno, who highlighted the necessity of regular updates to prevent vulnerabilities. 'This approach not only addresses immediate safety concerns but also aligns with the broader goal of building secure-by-design products, which are inherently resilient against cyber threats.'.
Moreover, the 2024 OSSRA report highlights the essential requirement for automated testing of safeguards, especially in handling the software supply chain. 'With 96% of analyzed code containing open-source components, manual testing becomes impractical at scale, necessitating automated methods like software composition analysis (SCA).'}. This highlights the significance of an automated patch management system in maintaining a strong protection framework, ensuring that all components are up-to-date and safe.
Conducting Regular Security Audits and Training
Performing routine assessments of protection systems is essential for determining the efficiency of malware defenses and wider protective strategies. These audits should assess configuration, performance, and compliance with industry best practices to ensure robust protection. For example, New America, a think tank handling sensitive data, emphasizes regular audits to prevent cyberattacks, having learned from past experiences.
Furthermore, continuous staff education on safety awareness and the importance of protective software is essential. Statistics show that a lack of time is a major barrier to effective training, yet personalized and on-demand learning experiences are increasingly expected in today's digital workforce. Educating employees on identifying phishing attempts and understanding the role of antivirus within the broader security strategy fosters a culture of vigilance. As noted by Director Easterly, enhancing cybersecurity hygiene through education can significantly bolster an organization's defense mechanisms.
Conclusion
In summary, implementing a comprehensive antivirus solution is essential for safeguarding sensitive information in today's digital landscape. Key components such as real-time protection, heuristic analysis, and a robust malware database create a multi-layered defense against evolving cyber threats. The integration of cloud-based threat intelligence further enhances the ability to detect and respond to new risks, underlining the necessity for organizations to stay informed about the latest developments in the threat landscape.
Effective configuration of antivirus solutions is equally critical. Tailoring settings to meet specific organizational needs, conducting scheduled scans, and configuring alerts can significantly improve both preventive and detective capabilities. The importance of balancing these elements is highlighted by industry studies, which demonstrate that organizations must refine their approaches to maximize protection against potential attacks.
Advanced threat detection techniques, including behavioral analytics and machine learning, provide organizations with the tools needed to identify and respond to unusual activities swiftly. By employing sandboxing environments and maintaining updated detection algorithms, organizations can remain vigilant in the face of increasingly sophisticated threats. Moreover, automating patch management and security updates minimizes vulnerabilities and enhances overall security posture, ensuring that systems are consistently fortified against exploitation.
Regular security audits and ongoing employee training further reinforce the effectiveness of antivirus measures. These practices not only evaluate the performance of security solutions but also foster a culture of awareness and vigilance among employees. By investing in comprehensive training and routine assessments, organizations can significantly enhance their cybersecurity defenses and adapt to the ever-evolving threat landscape.




