Introduction
In an age where cyber threats are increasingly sophisticated and pervasive, organizations must prioritize their cybersecurity strategies to safeguard sensitive data and maintain operational integrity. The CIS Critical Security Controls, developed by the Center for Internet Security, provide a structured framework of best practices designed to enhance an organization's security posture. This article delves into the implementation of these controls, offering insights on how to effectively integrate them into existing security frameworks, measure their effectiveness, and foster a culture of cybersecurity awareness among employees.
By adopting these essential measures, organizations can not only mitigate risks but also cultivate resilience against the evolving landscape of cyber threats.
Understanding CIS Critical Security Controls: A Foundation for Cybersecurity Success
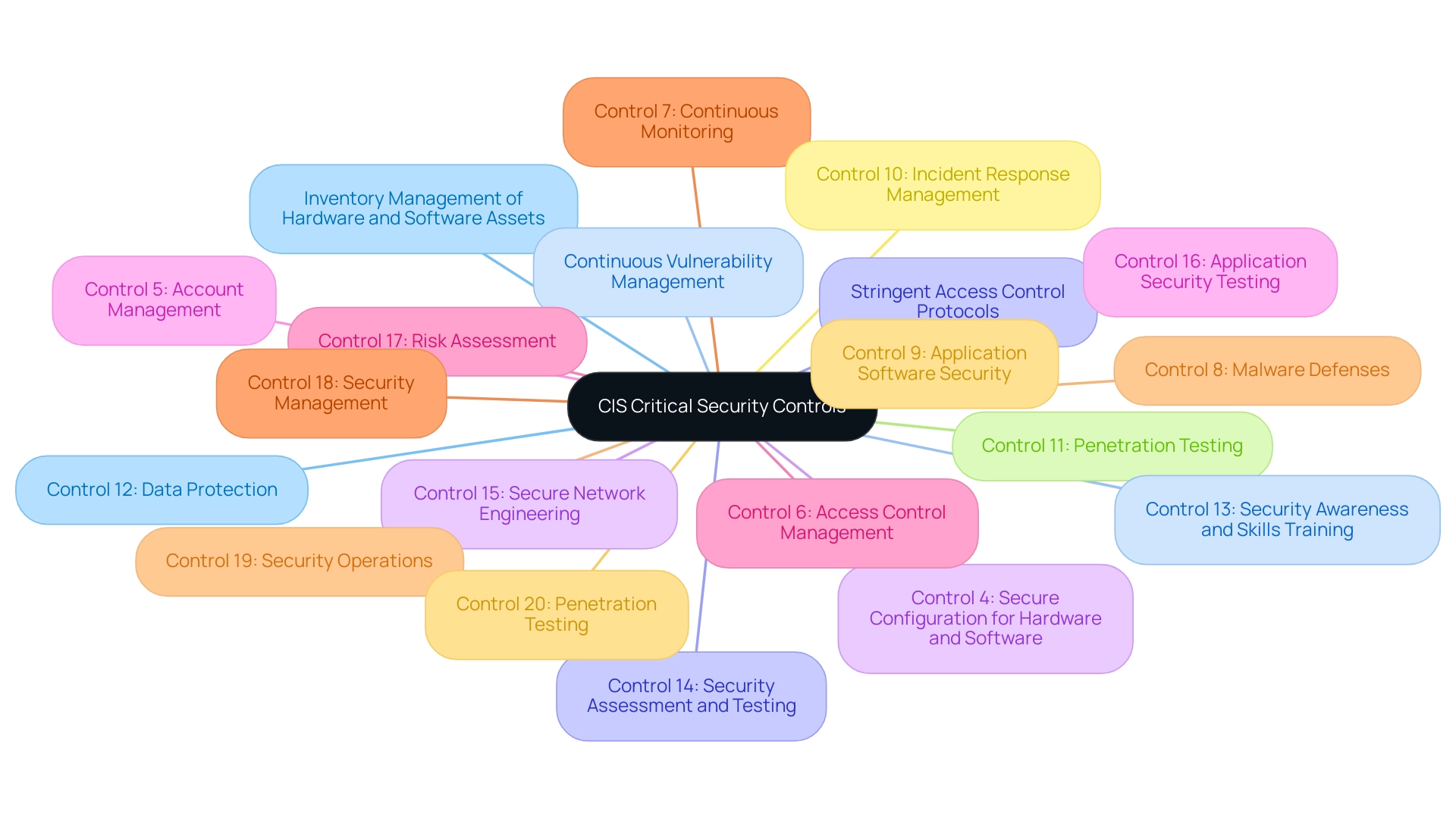
The CIS Critical Security Controls, created by the Center for Internet Security (CIS), constitute an extensive collection of best practices aimed at strengthening a company's security stance. These controls provide a prioritized approach for tackling common digital security threats, encompassing 20 essential measures that entities can adopt to protect their data and systems. Key controls include:
- Inventory management of hardware and software assets
- Continuous vulnerability management
- Stringent access control protocols
By systematically adopting these controls, entities can significantly mitigate risks and bolster their overall security framework. As the CIS emphasizes, "Identify points of breach and remediate as they are found." Recent statistics indicate that over 70% of entities have adopted at least some of the CIS Controls, showcasing their effectiveness in enhancing cybersecurity.
Furthermore, in 2024, recent news highlights the increasing importance of these controls as organizations face evolving cyber threats. The effectiveness of these controls is further demonstrated by the Order Systems Control Engine, which enhances visibility and security for network-connected devices, streamlining risk management processes. This structured approach not only diminishes vulnerabilities but also establishes the foundation for strong security initiatives, ensuring long-term protection and resilience.
Best Practices for Effective Implementation of CIS Controls
To implement the CIS Critical Security Controls effectively, entities must begin with a comprehensive assessment of their current cybersecurity posture. This entails identifying existing vulnerabilities and mapping them to the applicable CIS Controls. Here are several best practices for successful implementation:
-
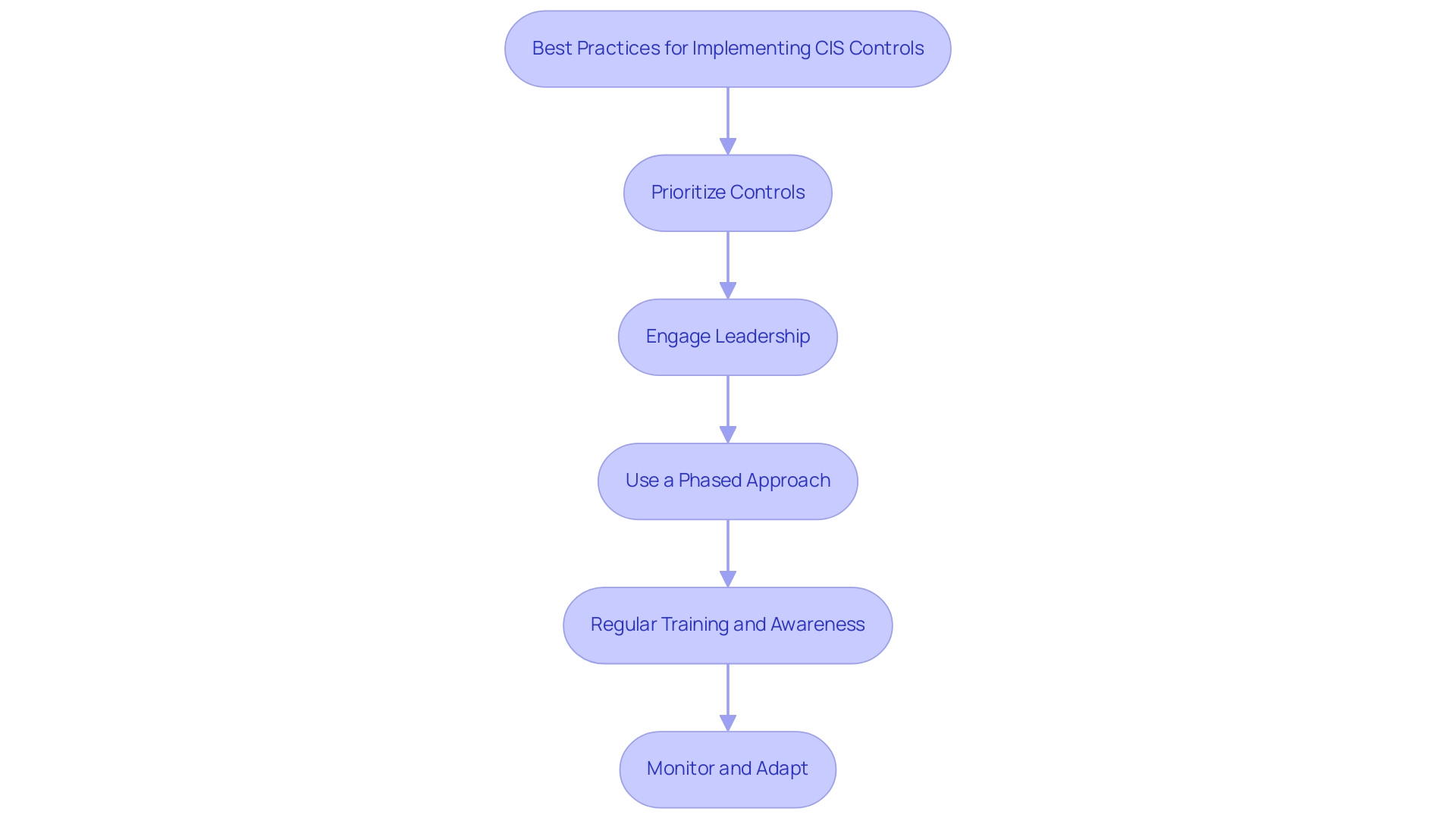
Prioritize Controls: Each entity faces unique risks and regulatory requirements. Prioritizing the implementation of controls based on specific business risks ensures that the most relevant controls are addressed first. According to recent studies, organizations that prioritize CIS Controls have reported a 30% reduction in security incidents within the first year of implementation.
-
Engage Leadership: Securing buy-in from senior management is crucial. Leadership must align security initiatives with business objectives and allocate the necessary funding and resources. Engaging leadership not only secures necessary resources but also ensures that digital security is regarded as a vital aspect of business strategy. A recent survey showed that entities with robust leadership involvement in protective initiatives experienced a 25% rise in overall effectiveness.
-
Use a Phased Approach: Implementing controls in phases, starting with the most critical ones, allows for immediate risk mitigation and resource management, leading to quick wins. For example, a case study involving a healthcare organization demonstrated that by focusing on the most critical controls first, they were able to enhance their security posture significantly within a few months.
-
Regular Training and Awareness: Continuous education and training for employees are vital. Promoting a security-focused culture through regular awareness programs guarantees that everyone comprehends the significance of digital safety and the specific controls being implemented. Organizations that conduct regular training have reported a 40% decrease in phishing-related incidents.
-
Monitor and Adapt: Establishing metrics to monitor the effectiveness of the controls is essential. Regular evaluations assist in recognizing gaps and ensuring that the security strategy evolves with emerging threats. A recent case study demonstrated that entities that routinely evaluated their security stance were capable of adjusting to new threats 50% quicker than those that did not.
The CIS Risk Assessment Method (CIS RAM) is an essential tool in this process. It offers entities with instructions, examples, templates, and exercises for conducting a cyber risk assessment. By adhering to these best practices, entities can strengthen their security frameworks, attain compliance with industry standards, and ultimately enhance data protection and risk management. As noted by cybersecurity experts, 'The CSC are beneficial aids for organizations that need to meet these complex industry standards or regulations.' This method not only strengthens protection but also aligns with the goal of maintaining robust cyber defenses in today's dynamic threat landscape.
Integrating CIS Controls into Existing Security Frameworks
Incorporating CIS Controls into existing protective frameworks necessitates a careful strategy that honors the current arrangement while improving protective measures. Organizations should start by evaluating existing protection protocols and determining which CIS Controls can complement or replace them. Here are some strategies for effective integration:
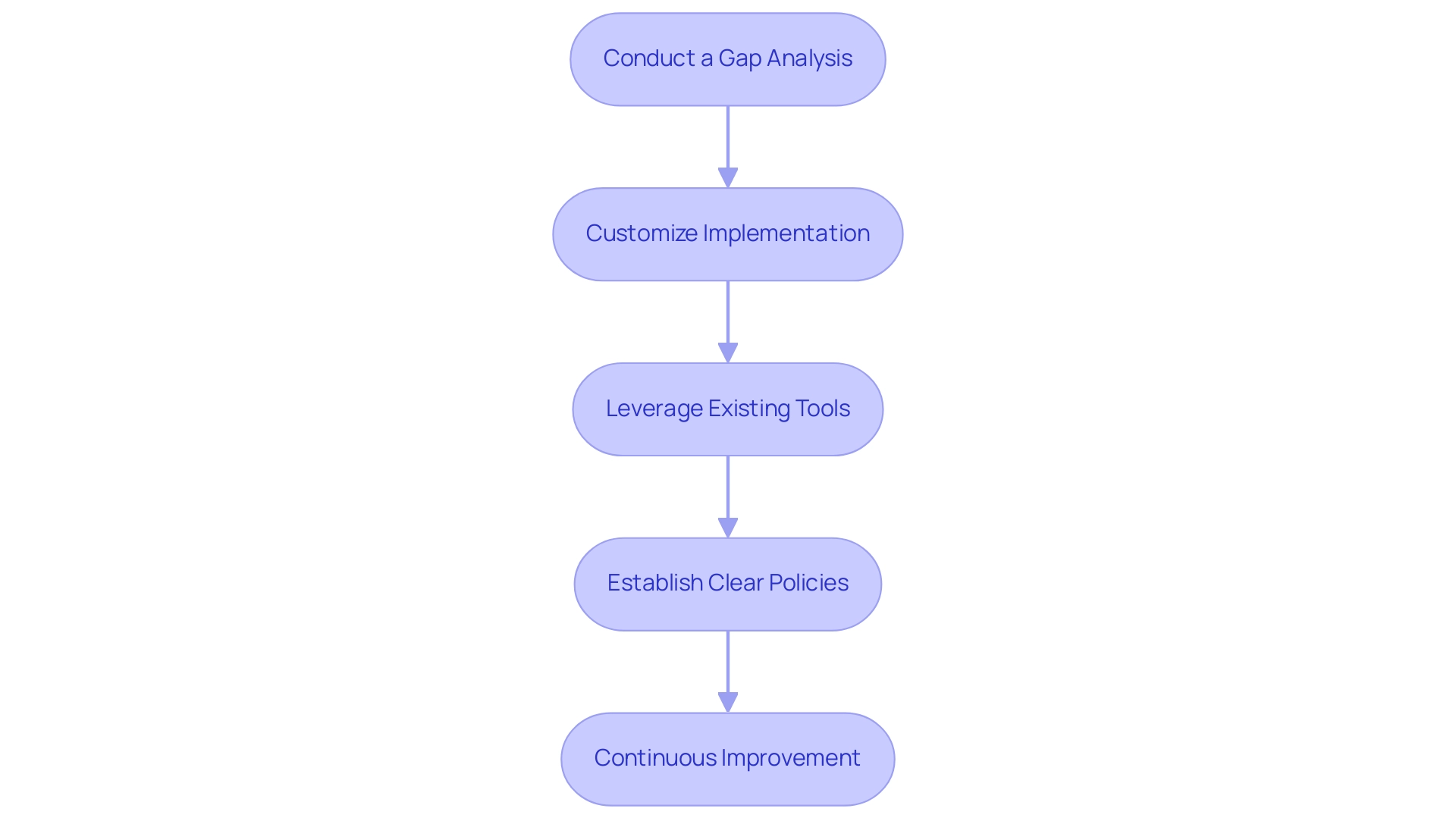
- Conduct a Gap Analysis: Identify the overlaps and gaps between current protective measures and the CIS Controls. This analysis will highlight areas that need immediate attention.
- Customize Implementation: Tailor the implementation of CIS Controls to fit the organization's unique environment. Consider factors such as industry regulations and specific business requirements.
- Leverage Existing Tools: Use available tools and technologies to implement CIS Controls wherever possible, minimizing the need for new investments and enabling a smoother transition.
- Establish Clear Policies: Update or create security policies that reflect the integration of CIS Controls, ensuring that employees are aware of their responsibilities under the new framework.
- Continuous Improvement: Treat the integration process as an ongoing journey rather than a one-time project. Regularly review the effectiveness of the integrated controls and make necessary adjustments to adapt to the evolving threat landscape.
Measuring the Effectiveness of CIS Controls
To ensure that CIS Controls are effectively mitigating risks, organizations must establish robust metrics and evaluation processes. Here are some best practices for measuring effectiveness:
-
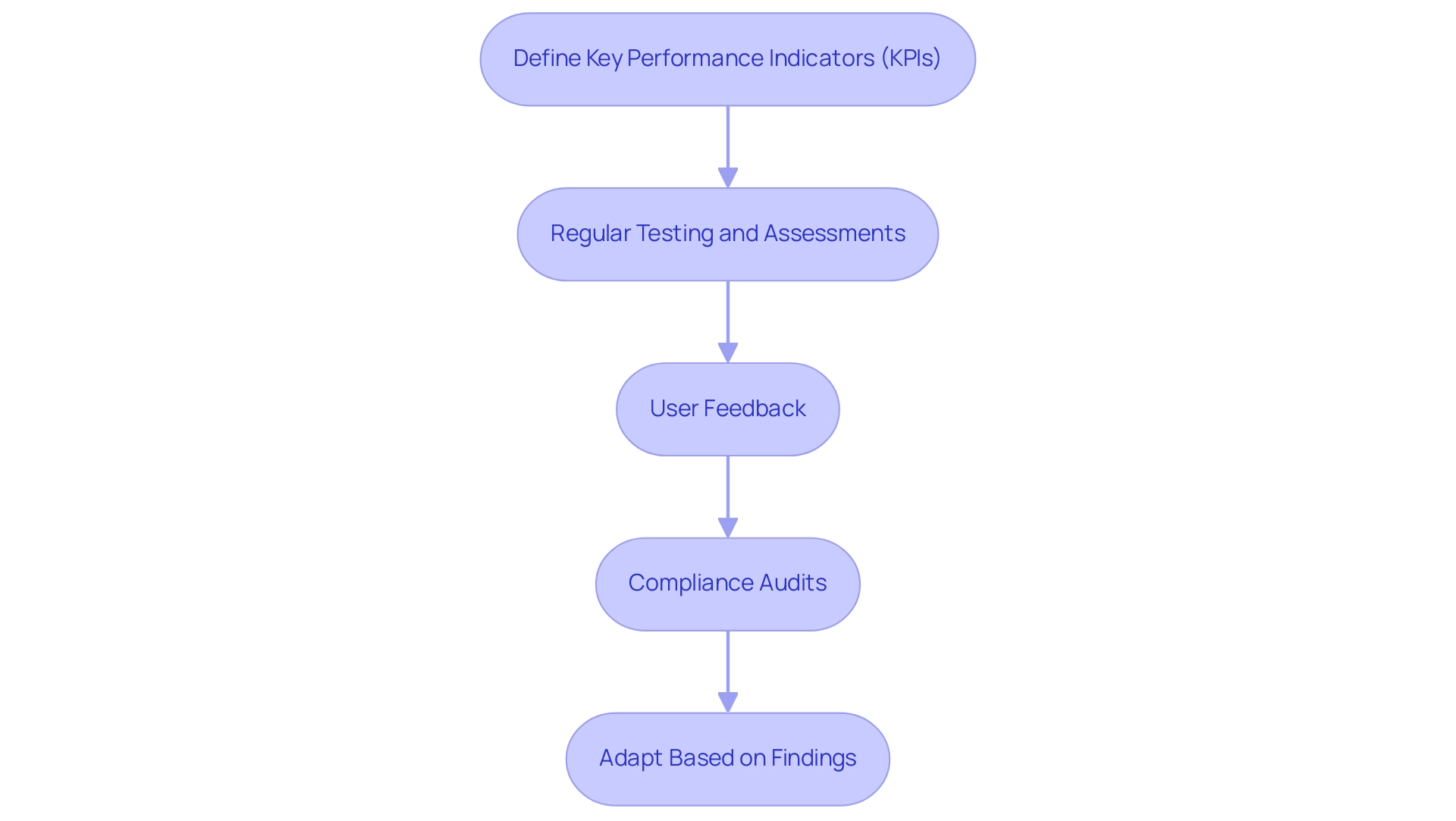
Define Key Performance Indicators (KPIs): Establish KPIs that align with your security objectives. An example of a crucial KPI is the Mean Time to Detect (MTTD), which assesses the time taken to become aware of potential security incidents. This metric is essential for gauging the responsiveness and efficiency of your security measures. Furthermore, statistics show that entities utilizing CIS Controls have experienced an enhancement in incident detection rates by as much as 30% within the initial year of implementation.
-
Regular Testing and Assessments: Conduct regular penetration testing and vulnerability assessments to evaluate the robustness of the controls in place. A Critical Severity finding might have a remediation window of 7 days, emphasizing the importance of timely and thorough testing.
-
User Feedback: Collect feedback from employees regarding the usability of implemented controls. Frontline insights can reveal gaps and opportunities for improvement, ensuring that the controls are practical and effective.
-
Compliance Audits: Perform regular audits to verify compliance with both internal policies and external regulations. This practice not only ensures adherence to standards but also evaluates the effectiveness of the cybersecurity tools and procedures in place. For instance, a case study on security audit compliance demonstrated that after implementing a regular audit schedule, a company identified and mitigated vulnerabilities that had previously gone unnoticed, resulting in a 25% reduction in security incidents.
-
Adapt Based on Findings: Utilize the data collected from these evaluations to make informed decisions about adjusting or enhancing controls. For example, one group discovered that their incident response time improved significantly after they adjusted their protocols based on findings from their vulnerability assessments. By consistently adjusting to emerging dangers, entities can sustain the efficiency of their security protocols. As Michael Swanagan, CISSP, notes,
By following the recommendations of measuring risk through metrics reporting, your IT teams and stakeholders will be able to clearly observe the outcomes and successes of the vulnerability management program.
By incorporating these best practices, organizations can ensure that their CIS Controls remain robust and effective in the face of evolving security threats.
Fostering a Culture of Cybersecurity Awareness
Establishing a strong culture of security awareness is essential for ensuring that every employee understands their role in protecting organizational assets. Here are practical steps to cultivate this culture:
-
Regular Training Programs: Establish continuous training initiatives that highlight the significance of online security and the specific CIS Controls in place. Interactive methods, such as simulations and hands-on workshops, can significantly enhance employee engagement and retention of essential concepts. Regular training and validation of security measures can prevent attacks and enhance overall security, as shown by numerous case studies emphasizing the consequences of neglecting fundamental security practices until after a breach happens. Statistics indicate that organizations with effective security training programs can lower the likelihood of incidents by as much as 70%.
-
Promote Best Practices: Consistently disseminate best practices and updates on emerging security threats through newsletters or internal communications. Keeping digital security at the forefront of employees' minds ensures they remain vigilant and informed about the latest risks and protective measures. Current trends for 2024 indicate a shift towards integrating gamification and real-time threat simulations in training programs to boost engagement.
-
Encourage Reporting: Foster an environment where employees feel safe reporting suspicious activities without fear of reprisal. This approach promotes accountability and ensures that potential threats are identified and addressed promptly.
-
Recognize and Reward: Acknowledge and reward employees who demonstrate exemplary practices in information security. Recognition programs not only motivate individuals but also establish a benchmark for others to emulate, highlighting the significance of proactive protective measures.
-
Lead by Example: Leadership must embody the significance of online security, as organizational culture often mirrors the behavior of its leaders. By prioritizing and modeling best practices for protection, leaders can cultivate a unified approach to safety that permeates all levels of the organization.
Eric Raymond, a protection expert, aptly states, 'Being able to break defenses doesn’t make you a hacker any more than being able to hotwire cars makes you an automotive engineer.' This underlines the importance of thorough and continuous training rather than relying on reactive measures post-breach. Recent initiatives in employee protection training programs have demonstrated that regular, comprehensive training significantly improves awareness and lowers the risk of incidents. Reinforcing these practices is crucial, as cybersecurity incidents are responsible for half of all supply chain disruptions. By prioritizing ongoing training and validation, organizations can bolster their security posture and mitigate the risks associated with cyber threats.
Conclusion
Mitigating cyber threats through the implementation of the CIS Critical Security Controls is essential for organizations striving to protect their sensitive data and maintain operational integrity. By prioritizing these controls, organizations can effectively address prevalent cybersecurity risks through a structured and comprehensive approach. The article highlights the importance of assessing current cybersecurity postures, engaging leadership, and adopting a phased implementation strategy to ensure that these critical measures are integrated smoothly into existing security frameworks.
Moreover, establishing metrics to measure the effectiveness of the CIS Controls is imperative. Regular assessments, user feedback, and compliance audits contribute to a dynamic security strategy that adapts to emerging threats. Fostering a culture of cybersecurity awareness among employees further strengthens defenses, as informed and engaged staff are integral to an organization's overall security posture.
In conclusion, the proactive adoption of the CIS Critical Security Controls not only enhances an organization's resilience against cyber threats but also fosters a culture of security that permeates all levels of the organization. By committing to continuous improvement and employee engagement, organizations can ensure robust protection in an ever-evolving cybersecurity landscape. The path to a secure future begins with these foundational practices, making it imperative for organizations to take decisive action today.




