Introduction
In a landscape where regulatory compliance and data security are paramount, CPA firms must navigate a complex array of IT requirements to protect sensitive client information and maintain trust. With the increasing scrutiny surrounding data protection and privacy laws, it becomes crucial for these firms to establish robust compliance frameworks that address both legal obligations and industry standards. This article delves into essential IT practices that can bolster compliance, enhance cybersecurity measures, and streamline client data management, all while leveraging technology to foster stronger client engagement.
By adopting these strategies, CPA firms can not only safeguard their operations but also position themselves as reliable stewards of client information in an ever-evolving digital environment.
Ensuring Compliance: Key IT Requirements for CPA Firms
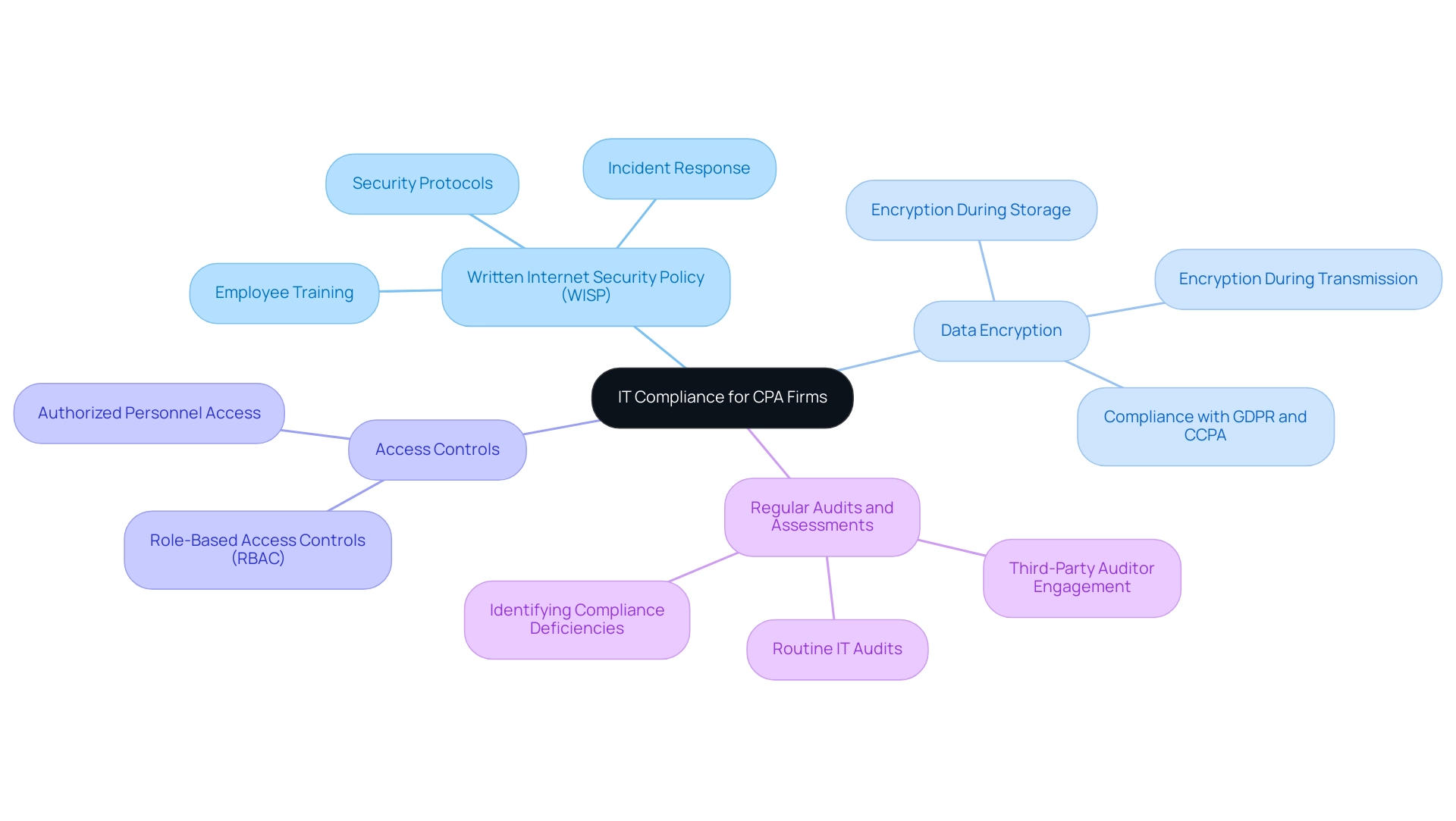
CPA organizations face rigorous compliance mandates related to data protection, financial reporting, and privacy laws, which are vital for maintaining investor trust and regulatory adherence. It is essential for funds and advisers to complete their first annual review of compliance policies no later than 18 months after adoption, underscoring the urgency of these requirements. Key IT compliance requirements include:
-
Written Internet Security Policy (WISP): A WISP is essential for outlining how a CPA practice protects sensitive customer information. This policy should encompass security protocols, employee training initiatives, and incident response strategies. Regular reviews are crucial to ensure the WISP adapts to evolving threats, thereby enhancing its effectiveness.
-
Data Encryption: It is imperative that all sensitive customer data—such as tax documents and financial statements—is encrypted both during transmission and storage. This practice is essential for protecting against unauthorized access and is a pivotal compliance requirement under regulations such as the GDPR and CCPA.
-
Access Controls: Implementing role-based access controls (RBAC) ensures that only authorized personnel have access to sensitive information. This not only protects customer data but also assists in adhering to industry regulations, thereby strengthening the organization's integrity.
-
Regular Audits and Assessments: Conducting routine IT audits is instrumental in identifying compliance deficiencies and security vulnerabilities. Engaging third-party auditors can provide an objective assessment of compliance status and recommend necessary enhancements.
By instituting comprehensive IT compliance practices, CPA firms can significantly mitigate risks, bolster client trust, and fulfill their legal obligations while ensuring the security of client information, aided by effective CPA firm IT support. As noted by Jiaqi Zhou, effective accounting software, such as QuickBooks and FreshBooks, can streamline compliance efforts by providing essential tools for managing reporting needs and operational efficiency. For instance, major accounting software platforms provide features that assist companies in maintaining compliance with regulations, demonstrating the significance of choosing the right software solution.
Strengthening Security: Best Cybersecurity Practices for CPA Firms
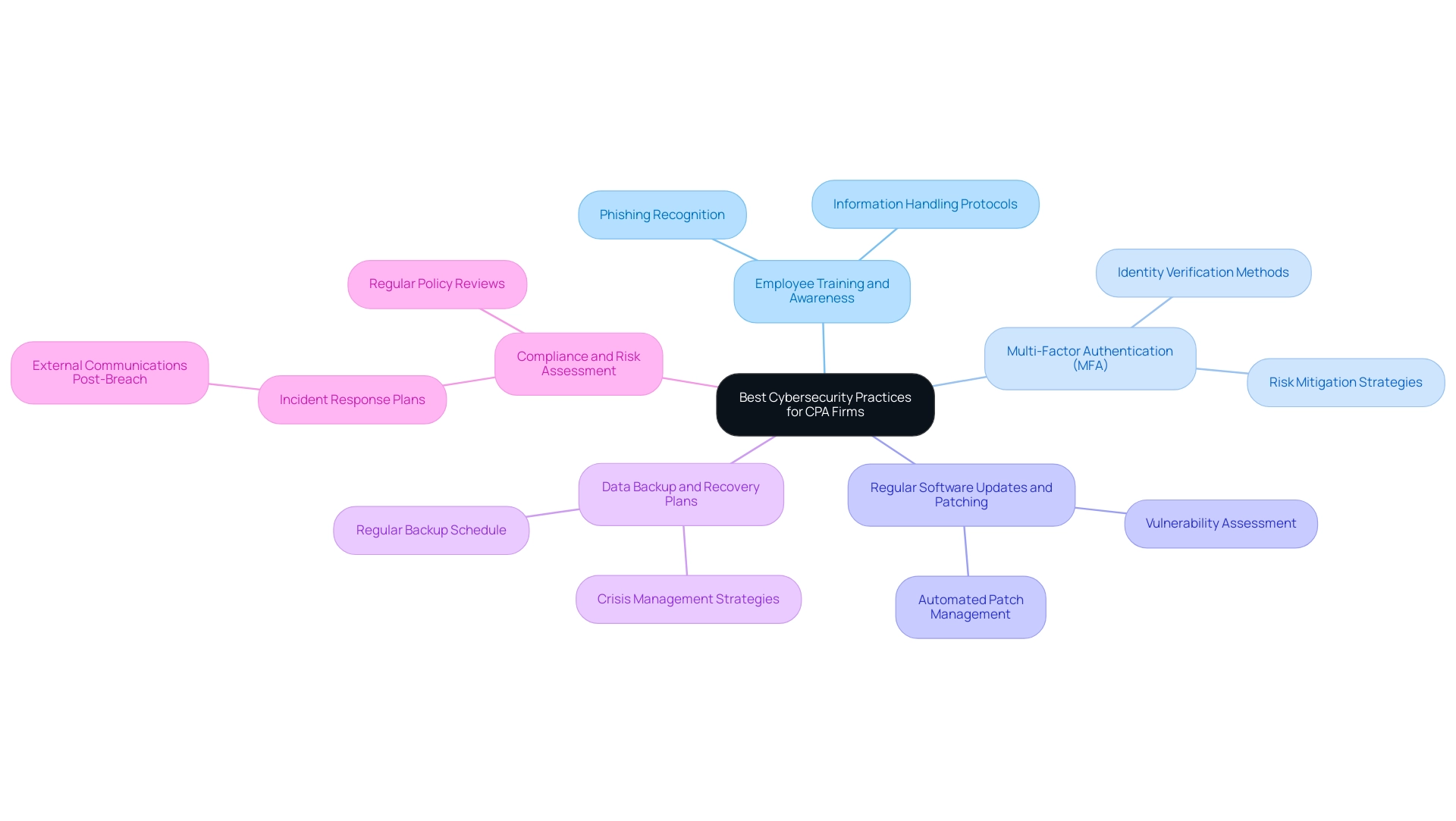
To safeguard sensitive financial information, CPA organizations must apply a proactive cybersecurity approach that includes several best practices:
-
Employee Training and Awareness: Regular training sessions focusing on recognizing phishing attempts, social engineering tactics, and information handling protocols are critical. Employees need to understand their integral role in maintaining cybersecurity, as a well-informed workforce is the first line of defense against cyber threats.
-
Multi-Factor Authentication (MFA): The implementation of MFA provides an additional layer of security, requiring users to verify their identity through multiple authentication methods. This significantly mitigates the risk of unauthorized access to sensitive accounts, aligning with the increasing demand for robust security measures in the industry.
-
Regular Software Updates and Patching: Keeping software up to date is essential to safeguard against vulnerabilities. Employing an automated patch management system ensures that updates are applied promptly, thereby minimizing exposure to potential threats. This proactive approach is vital for maintaining a secure IT infrastructure.
-
Data Backup and Recovery Plans: Regular data backups are essential for CPA organizations to ensure swift recovery from data loss incidents, whether due to cyberattacks or system failures. A clearly outlined recovery strategy not only reduces downtime but also maintains customer trust, demonstrating that the organization can effectively handle crises. Engaging managed IT service providers for CPA firm IT support offers CPA organizations access to advanced cybersecurity technologies and specialized expertise. These services can effectively identify vulnerabilities and implement comprehensive security measures tailored to the organization's specific needs, enhancing overall security posture.
By prioritizing these cybersecurity measures, CPA practices can protect their customers’ sensitive information, maintain compliance with regulatory requirements, and establish themselves as reliable custodians of financial information. As highlighted in recent discussions, organizations must regularly review and update their cybersecurity policies based on risk assessments and evolving best practices. This is particularly crucial in light of regulations such as Part 500, which mandates that Covered Entities address external communications in their incident response plans following a breach.
Additionally, CPA organizations must recognize that their internal networks—including email, document hosting, and related services—are vital components that require robust protection. Furthermore, the Cybersecurity Regulation emphasizes the necessity of reviewing risk assessments in response to material changes in business or technology, as seen in case studies where mergers, acquisitions, and outsourcing key processes have significantly altered cyber risk landscapes.
Implementing Effective Client Data Management Practices
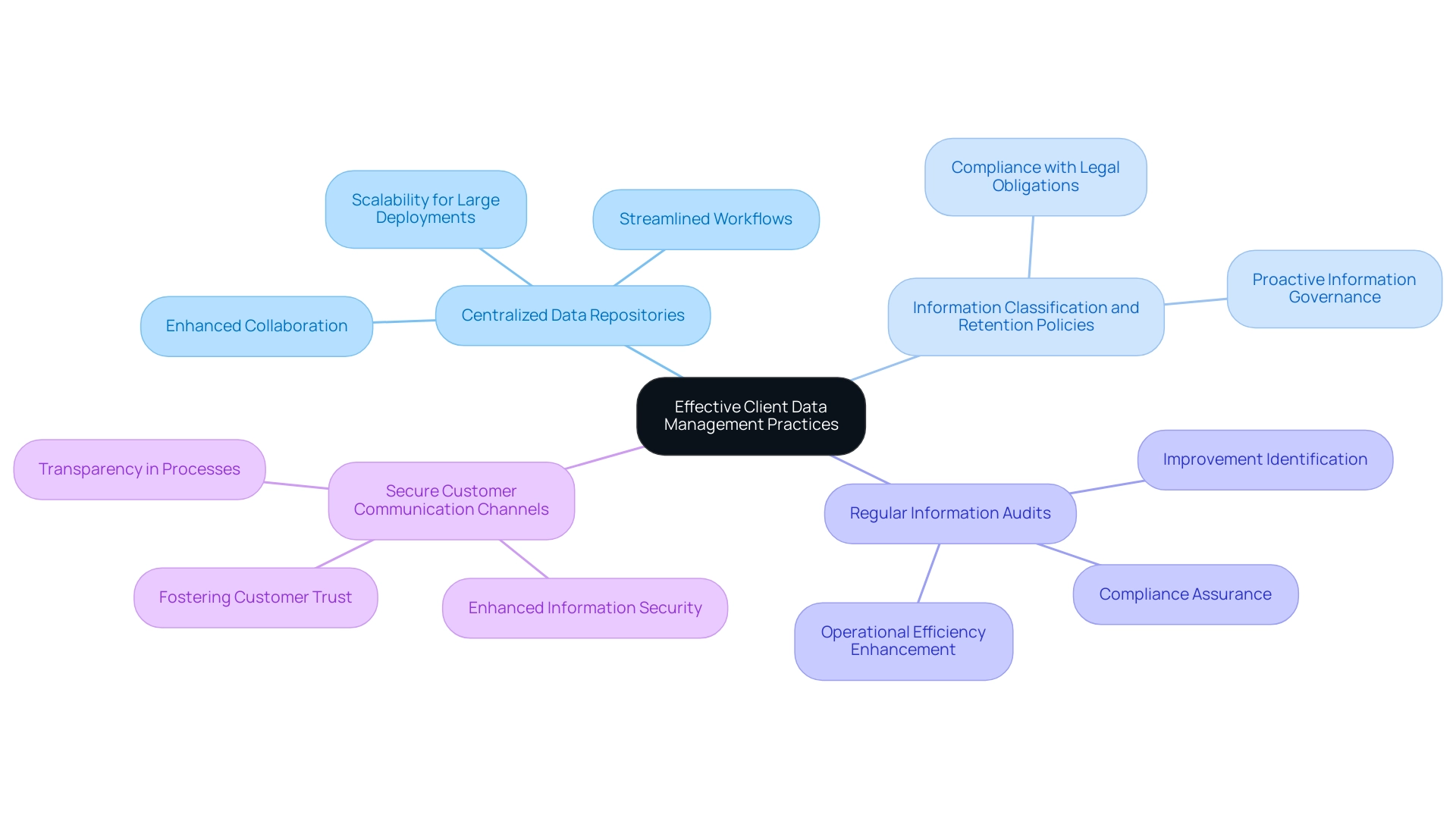
Efficient management practices for customers' information are crucial for CPA organizations, as their CPA firm IT support ensures both precision and safety in the handling of sensitive financial details. Key practices that contribute to these goals include:
-
Centralized Data Repositories: Implementing a centralized document management system enables CPA organizations to efficiently store, manage, and access records of customers. This strategy not only reduces the risk of information loss but also fosters enhanced collaboration among team members. As noted in expert discussions, centralized repositories allow firms to streamline their workflows, ultimately improving service delivery and client satisfaction. Notably, the enterprise plan provides custom solutions for large deployments, underscoring the scalability of these management systems.
-
Information Classification and Retention Policies: Establishing robust classification protocols is crucial for identifying and appropriately handling sensitive information. Furthermore, establishing clear retention policies guarantees that organizations stay compliant with legal obligations by specifying how long various categories of information should be preserved. This proactive approach to information governance is vital in today's regulatory landscape.
-
Regular Information Audits: Conducting periodic evaluations of information management practices with CPA firm IT support allows CPA firms to pinpoint areas needing improvement, ensuring compliance with industry standards and enhancing operational efficiency. Such audits offer insights into the effectiveness of current practices and guide necessary adjustments, reinforcing a commitment to excellence in information management. The study titled "Future Research Directions" emphasizes the necessity for additional investigation on trust factors in information management, particularly concentrating on individual traits and the influence of communication, which is crucial for comprehending customer relationships.
-
Secure Customer Communication Channels: Utilizing secure channels for sharing sensitive customer information, such as encrypted emails or secure portals, significantly enhances information security and fosters customer trust. The significance of secure communication cannot be overstated, as it reassures users that their information is safeguarded against unauthorized access. As highlighted by Petersen I. et al. (2014), perceptions of informed consent play a critical role in consumer trust and information handling practices, and companies must prioritize transparency in their processes.
By adopting these effective information management practices, CPA firms can enhance their reputation for reliability and professionalism, and with CPA firm IT support, they can also streamline their operations and protect customer information. The increasing focus on centralized information management reflects a broader trend towards enhanced efficiency in accounting practices, strengthening trust in customer relationships. As NP3 aptly stated,
Look, if I am part of a group, and I have to make a choice... What concerns me is what they do with it.
You must give them that trust, but I find that a bit difficult.
This sentiment underscores the critical need for transparency and reliability in data management strategies.
Utilizing Technology for Enhanced Client Engagement
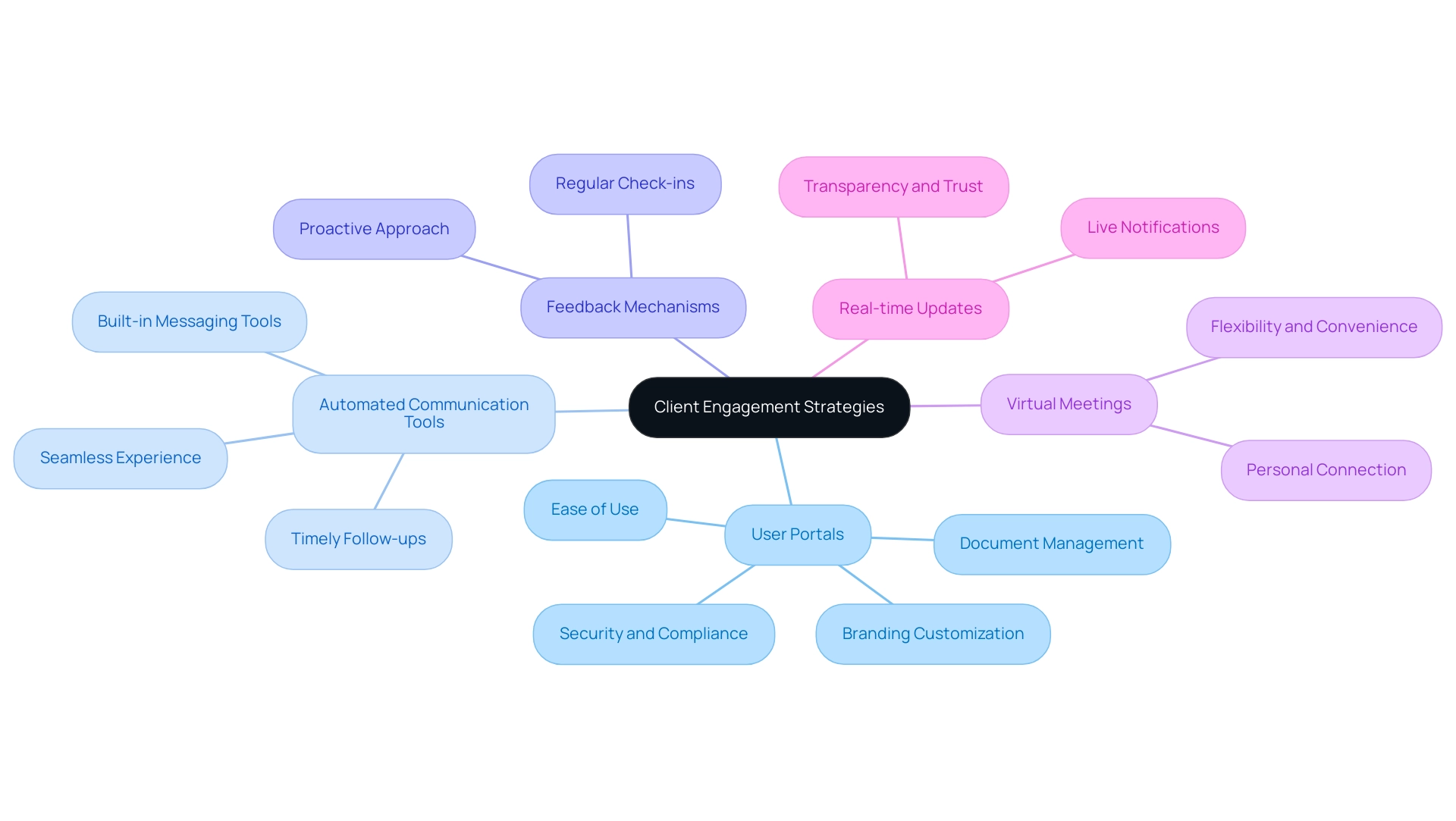
To optimize customer engagement, CPA firms should adopt several technology-driven strategies:
-
User Portals: The implementation of secure online user portals enables individuals to conveniently access their financial information, documents, and reports. This not only elevates customer satisfaction but also enhances communication efficiency. Key features of effective customer portals include security and compliance, ease of use, branding customization, and robust document management. Financial Cents exemplifies this with its secure folder sharing that incorporates permission controls, ensuring both security and user-friendliness.
-
Automated Communication Tools: Utilizing CRM systems equipped with automated communication features can significantly enhance user interactions. These tools facilitate timely follow-ups, reminders, and updates, creating a seamless experience for users. As highlighted by Kellie Parks, a CPB,
There isn’t a delay… there isn’t another need to log in or refresh. It actually just keeps adding those tasks even as they are looking at them, showcasing the efficiency of real-time updates in enhancing engagement. Additionally, incorporating built-in messaging tools enhances effective communication and collaboration within the organization, enabling swift replies to customer inquiries. -
Feedback Mechanisms: Establishing robust channels for feedback, such as surveys or regular check-ins, allows CPA firms to assess satisfaction effectively and pinpoint areas that require improvement. This proactive approach not only strengthens relationships but also fosters a culture of continuous improvement.
-
Virtual Meetings: The adoption of virtual meeting platforms has revolutionized interactions by providing flexibility and convenience for consultations while maintaining a personal connection. This adaptability is crucial in today’s fast-paced environment, where customers appreciate the ease of accessing services from their preferred locations.
-
Real-time Updates: Keeping customers informed with real-time activity updates is essential for transparency and trust. The case study on Financial Cents emphasizes this need, as it provides live notifications for every action taken, ensuring clients stay informed throughout their engagement with the company.
By strategically leveraging these technological advancements and incorporating CPA firm IT support, CPA firms can significantly enhance their service delivery and cultivate enduring relationships with clients, ultimately driving sustainable business growth.
Establishing a Robust IT Support Framework
To establish a robust IT support framework, CPA firms should consider the following essential components:
-
Dedicated IT Support Team: Assembling a dedicated team of IT professionals is crucial for promptly addressing technical issues, thereby minimizing disruptions to daily operations. A focused team can respond effectively to challenges, ensuring that the organization's IT infrastructure runs smoothly and efficiently. Investigating potential IT support providers is crucial for choosing a team that satisfies the specific requirements of the company.
-
Service Level Agreements (SLAs): The implementation of SLAs with defined response times and resolution targets is vital for setting clear expectations for IT support services. This not only enhances accountability but also fosters a trustworthy relationship between the company and its IT support providers, ensuring that service standards are consistently met.
-
Regular Maintenance and Monitoring: Establishing a routine for system maintenance and monitoring is imperative to identify potential issues before they escalate. This proactive method enhances system reliability and performance, protecting the organization against unexpected downtime that could hinder productivity. Notably, with a robust IT support framework, users can generate up to 100 Custom Charts/Dashboards, significantly improving operational efficiency.
-
Feedback and Continuous Improvement: Encouraging feedback from staff regarding IT support services promotes a culture of continuous improvement. This iterative process ensures that the support framework evolves in alignment with the organization's changing needs, ultimately leading to enhanced satisfaction and operational efficiency.
As Apptivo states, "The implementation takes place through 6 Stages beginning with a Kick-Off call," highlighting the structured approach necessary for establishing effective IT support frameworks.
By implementing a comprehensive CPA firm IT support framework, CPA organizations can significantly enhance their operational efficiency, reduce downtime, and maintain a high level of service delivery. This strategic investment not only addresses immediate technical concerns but also positions the organization for future growth and adaptation in a rapidly evolving technological landscape.
Monitoring and Assessing IT Performance
Effective monitoring and assessment of IT performance in CPA firms hinges on several critical practices:
-
Key Performance Indicators (KPIs): Establishing relevant KPIs is essential for measuring the effectiveness of IT strategies and initiatives. These metrics provide clear benchmarks for evaluating how technology contributes to overall business objectives, allowing companies to make informed decisions. With over $1.5B paid on Paydirt, the financial implications of effective IT performance monitoring cannot be overstated.
-
Regular Performance Reviews: Conducting systematic performance reviews of IT systems—including both hardware and software—ensures that technology remains both relevant and efficient. Such evaluations help identify potential areas of improvement and ensure that the IT infrastructure aligns with the evolving needs of the firm.
-
User Feedback: Actively gathering user feedback regarding interactions with technological tools, such as portals and communication platforms, offers invaluable insights for ongoing improvements. This feedback loop is crucial for enhancing user experience and fostering stronger client relationships.
-
Benchmarking Against Industry Standards: Comparing IT performance metrics with industry standards enables CPA organizations to pinpoint gaps and identify areas for enhancement. This practice not only aids in maintaining competitiveness but also provides a framework for continuous improvement in service delivery and operational efficiency.
As Adam Nubern, Owner of Nuventure CPA, reflects, "A Semester at Sea in college and the loss of a close family member made me realize there’s more to life than clocking hours in a cubicle." This perspective underscores the importance of IT performance in enhancing work-life balance and fulfillment for professionals in the field.
By implementing these robust monitoring and assessment practices, along with utilizing tools such as Paydirt for time tracking and invoicing, CPA firms can enhance their CPA firm IT support strategies to ensure effectiveness, ultimately leading to improved service delivery and increased operational efficiency.
Conclusion
In today's environment, where data security and regulatory compliance are paramount, CPA firms must adopt comprehensive IT practices to safeguard sensitive client information. Key components include establishing a Written Internet Security Policy (WISP), utilizing data encryption, and implementing robust access controls. Regular audits are essential for identifying vulnerabilities and ensuring compliance with evolving regulations.
Additionally, best cybersecurity practices—such as employee training, multi-factor authentication, and effective data backup—are vital for protecting client data and maintaining trust. Engaging managed IT services can provide firms with advanced technologies and expertise to enhance their cybersecurity posture.
Effective client data management practices are equally crucial. Centralized data repositories and secure communication channels streamline operations and strengthen client relationships through transparency and reliability.
Furthermore, leveraging technology-driven strategies, such as secure client portals and automated communication tools, significantly enhances service delivery and client satisfaction.
By prioritizing robust IT support frameworks and continuous performance monitoring, CPA firms can adapt to the complexities of the digital landscape. These strategic initiatives not only fulfill legal obligations but also foster lasting trust with clients, positioning firms for a secure and prosperous future.




