Introduction
In the rapidly evolving landscape of container management, Kubernetes clusters have emerged as a pivotal framework for organizations seeking to optimize their application deployment and management processes. By enabling seamless orchestration of containerized applications, Kubernetes not only enhances operational efficiency but also addresses the pressing need for robust security measures in an increasingly complex IT environment.
As organizations prepare for the anticipated shifts in 2024, understanding the critical components of Kubernetes, such as:
- Pods
- Services
- Deployments
becomes essential. This article delves into the fundamental aspects of Kubernetes cluster management, best practices for resource allocation, and the tools that facilitate streamlined operations, while also exploring the challenges and security considerations that organizations must navigate in a multi-cloud landscape.
Through a comprehensive examination of these topics, insights are provided to empower organizations to leverage Kubernetes effectively and safeguard their digital assets.
Understanding Kubernetes Clusters: The Foundation of Container Management
Container cluster management is essential for orchestrating containers, enabling organizations to deploy, manage, and scale containerized solutions with exceptional efficiency. A standard container cluster management system consists of a master node that manages the operations and several worker nodes focused on executing the services themselves. Understanding the intricacies of key components such as Pods, Services, and Deployments is vital for effective container cluster management.
- Pods: Identified as the tiniest deployable units within the container orchestration platform, can encapsulate one or more containers, making them essential for software functionality.
- Services: Conversely, enable seamless communication between Pods, ensuring that interconnected systems can operate smoothly.
Recent data indicates that as of 2023, familiarity with container orchestration has become increasingly prevalent, with a notable shift toward adoption anticipated in 2024.
For instance, entities are leveraging Replica Sets to maintain the desired number of Pods consistently running, thereby enhancing the reliability and availability of their applications. This investment in Kubernetes not only streamlines operations but also corresponds with the increasing trend of IT entities improving their protection frameworks in response to sophisticated cyber threats. At present, 10% of entities have separate DevOps and security teams with minimal collaboration, highlighting a critical area for improvement in operational synergy.
By implementing robust collaboration around security-focused processes, entities can safeguard sensitive data across hybrid cloud environments while adhering to regulatory standards. As highlighted by Komodor, the benefits of adopting container orchestration in 2024 are substantial, emphasizing the necessity for entities to adjust and progress their infrastructure. Furthermore, many IT companies are investing in advanced security platforms, as illustrated by the case study titled Investment in Security Platforms, which emphasizes the importance of these investments in protecting sensitive data.
Best Practices for Effective Kubernetes Cluster Management
To effectively manage Kubernetes clusters, organizations should adopt a set of best practices centered on container cluster management that optimizes resource allocation and enhances operational efficiency. Implementing resource quotas and limits is crucial, as this approach prevents any single program from monopolizing resources. For instance, defining CPU usage at a limit of 2 and memory at 2 GiB within Pod specifications is essential for maintaining balanced resource distribution.
This statistic highlights the importance of setting clear boundaries to ensure fair resource allocation across applications. A notable case within this context involved a situation where an error message indicated the inability to create a second Pod due to exceeding the memory request quota. By changing the Pod's Priority Class to high, the creation was successful, illustrating the importance of prioritizing resources effectively.
Furthermore, utilizing namespaces is a best practice that allows for logical separation between different environments, such as development, testing, and production. This segregation not only mitigates potential conflicts but also enhances security, ensuring that changes in one environment do not inadvertently affect others. Regular monitoring with tools like Prometheus is recommended to identify performance bottlenecks early, enabling teams to respond proactively and maintain optimal cluster performance.
Furthermore, automating deployments through GitOps practices fosters consistency and significantly reduces the risk of human error, which is essential for effective container cluster management and maintaining the integrity of the orchestration environment. As highlighted by DevOps Engineer Subham Pradhan, "Using these commands, you can effectively manage Resource Quotas in the container orchestration platform," which emphasizes the practical use of these best practices. An example of effective container orchestration solutions for application development and testing is illustrated in the case study titled 'Sandbox,' which provides a safe environment for developers to experiment and learn without affecting production systems.
These guidelines represent foundational steps in mastering container cluster management, aligning with the best practices for 2024.
Tools and Technologies for Streamlined Container Cluster Management
A variety of tools are available for container cluster management, each designed to enhance operational efficiency and security. The orchestration dashboard offers an accessible online interface that simplifies container cluster management and enables real-time observation of cluster resources. Complementing this, Helm serves as an essential tool for container orchestration application management, utilizing charts to simplify deployments and updates.
As noted by expert Medha Mehta, by leveraging the right tools, you can ensure your container cluster management environments are running smoothly. For robust protection, solutions such as Aqua Security and Twistlock provide comprehensive vulnerability scanning and compliance monitoring, addressing critical safety needs in container environments. Additionally, Kube-bench is an automated tool that checks container clusters against security best practices, further enhancing the security posture of container cluster management.
Integrating CI/CD pipelines with tools like Jenkins or GitLab CI not only automates deployment processes but also enhances the speed and reliability of software delivery. Furthermore, in 2024, advancements in container cluster management tools—such as Mani-diffy, which effectively manages a hierarchy of Argo CD application templates, providing flexibility and control over application deployments—demonstrate the ongoing evolution of this field. Notably, Amazon EKS pricing starts at $0.10/hour per cluster, highlighting important cost considerations for enterprises.
Additionally, case studies like that of Klutch, which extends Crossplane for managing resources across multiple Kubernetes clusters, highlight the practical benefits of these tools in facilitating efficient resource management. Leveraging these technologies not only supports continuous integration and delivery practices but also positions enterprises to thrive in an increasingly competitive landscape.
Navigating Challenges in Multi-Cloud Container Management
Navigating the complexities of container cluster management in a multi-cloud environment introduces a range of challenges, including data consistency, network latency, and compliance with regulatory standards. In 2024, entities will face increasing pressure to address these issues, as data integrity and security become paramount. According to Taylor Karl, next year, 54% of organizations plan to move their workloads to cloud-based systems, highlighting the urgency of addressing multi-cloud challenges.
Adopting a cloud-agnostic strategy is essential; utilizing frameworks such as Kubernetes Federation enables effective container cluster management across diverse cloud providers. This approach not only enhances operational efficiency but also mitigates risks associated with vendor lock-in. Furthermore, implementing comprehensive monitoring solutions, like Dynatrace, offers critical visibility into application performance across various cloud platforms, facilitating timely adjustments and optimizations.
A robust governance framework is equally vital, ensuring compliance with regulations and protecting sensitive data from breaches. Furthermore, entities should be aware of the most prevalent threats in the cloud and on-site identified for 2024, which highlights the significance of a proactive defense strategy. Conducting regular reviews of cloud vendor capabilities can optimize costs and performance.
For instance, recent success stories reveal that companies like Drift have effectively reduced their annual cloud expenditure by $2.4 million through strategic management practices. These examples underscore the necessity of leveraging the best available services in the cloud landscape, ultimately driving organizational success in a multi-cloud strategy.
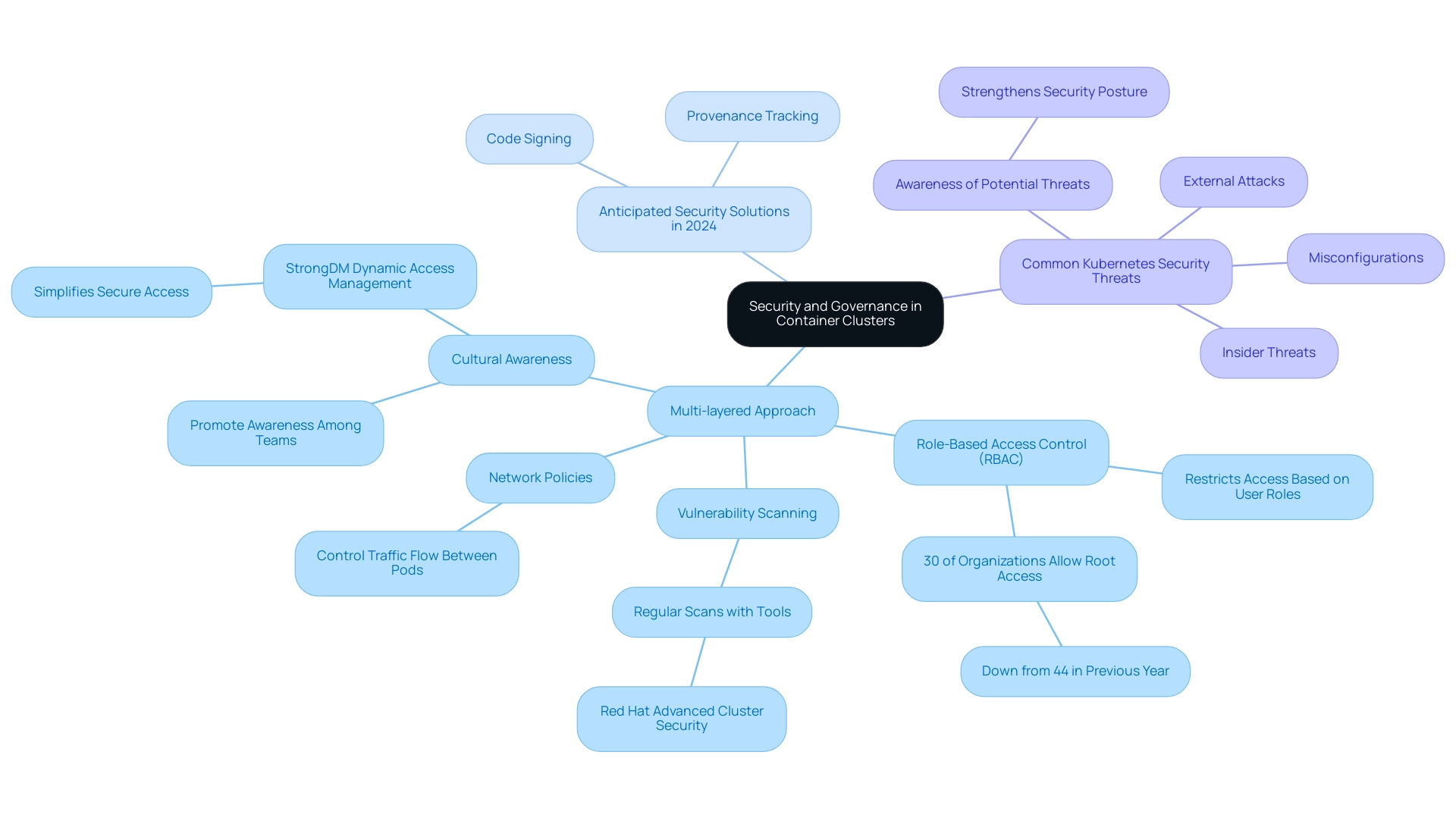
Ensuring Security and Governance in Container Clusters
To guarantee strong protection in container cluster management, companies must implement a thorough, multi-layered approach. Central to this approach is the implementation of role-based access control (RBAC), which restricts access to critical resources based on designated user roles. Recent statistics suggest a positive change, with only 30% of entities permitting 71% or more of their workloads root access in 2024, down from 44% the prior year—an encouraging trend towards improved safety practices.
Tools like Red Hat Advanced Cluster Security are invaluable for conducting regular vulnerability scans and compliance checks, enabling organizations to identify and mitigate potential risks effectively. Furthermore, the establishment of stringent network policies is crucial for controlling traffic flow between Pods, thereby enhancing overall protection. Regular audits of container configurations, paired with adherence to the principle of least privilege, significantly reduce exposure to threats.
StrongDM Dynamic Access Management simplifies secure access across infrastructure, including Kubernetes, ensuring that only approved, immutable images are deployed. As John Martinez, a Technical Evangelist, aptly states,
Make it easy: StrongDM enables the deployment of only approved, immutable images
This highlights that simplifying processes can improve compliance.
Lastly, promoting a culture of awareness among both developers and operations teams is vital, ensuring that protective considerations are integrated into every phase of application development. With the expected increase in supply chain protection solutions in 2024, including code signing and provenance tracking, organizations must stay alert to safeguard their container cluster management environments from third-party code infiltration. This vigilance is particularly critical in addressing common risks, such as misconfigurations, insider threats, and external attacks, as highlighted in the case study on common Kubernetes vulnerabilities.
Understanding these risks is essential for implementing effective security controls and strengthening the overall security posture.
Conclusion
Kubernetes clusters stand at the forefront of container management, offering organizations a powerful framework to enhance their operational efficiency while addressing critical security needs. As explored throughout the article, understanding the fundamental components, such as Pods, Services, and Deployments, is essential for effective Kubernetes management. By adhering to best practices in resource allocation and leveraging advanced tools, organizations can optimize their cluster operations and safeguard their digital assets against evolving threats.
The challenges of managing containerized applications in a multi-cloud environment necessitate a proactive approach. Organizations must adopt cloud-agnostic strategies and comprehensive monitoring solutions to ensure data integrity and compliance with regulatory standards. By fostering collaboration between DevOps and security teams, businesses can create a robust governance framework that not only mitigates risks but also enhances overall performance.
As organizations prepare for the anticipated shifts in 2024, the integration of security measures and resource management practices will be crucial. By prioritizing security awareness and investing in advanced technologies, organizations can navigate the complexities of container management while positioning themselves for success in an increasingly competitive landscape. Embracing Kubernetes is not just a trend; it is a strategic imperative that will empower organizations to thrive in the digital age.




