Introduction
In an age where data breaches and cyber threats loom large, the establishment of robust laptop usage policies has become a critical necessity for organizations. These guidelines not only protect sensitive information but also enhance operational efficiency, ensuring that employees can navigate the digital landscape with confidence. By clearly outlining acceptable behaviors and implementing stringent security measures, companies can mitigate risks associated with laptop use, particularly in the context of remote work.
This article delves into the essential components of effective laptop policies, from integrating compliance and security protocols to fostering a culture of awareness among employees, providing a comprehensive framework for organizations aiming to safeguard their digital assets.
Establishing Clear Guidelines for Company Laptop Usage
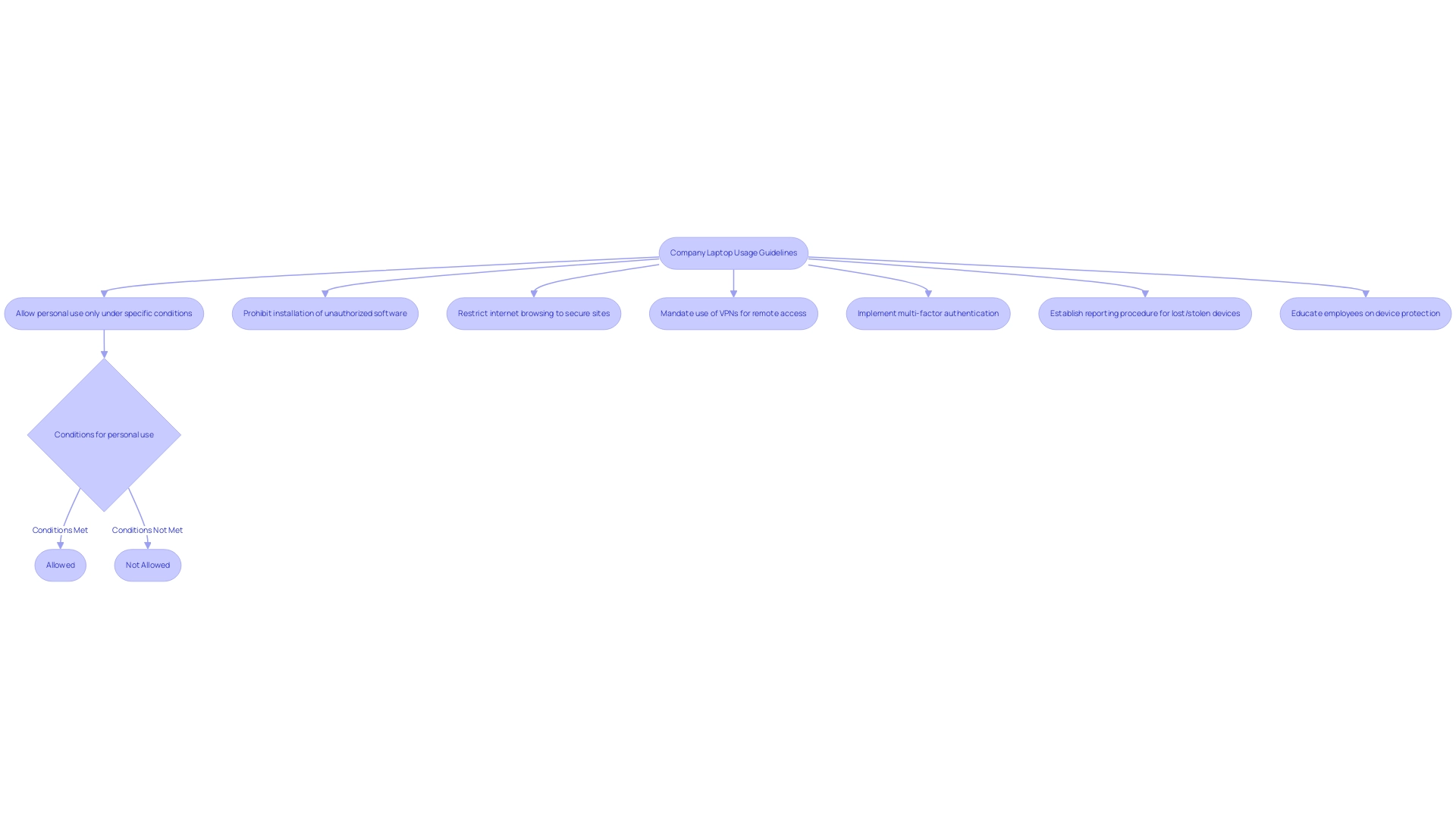
Establishing comprehensive usage guidelines for company devices is essential for safeguarding sensitive data and ensuring operational efficiency. These guidelines must clearly delineate acceptable and prohibited behaviors, such as:
- Allowing personal use of computers only under specific conditions
- Prohibiting the installation of unauthorized software
- Restricting internet browsing to secure sites
For instance, an effective policy might state that staff can use their laptops for personal tasks during breaks but must refrain from accessing social media or streaming services during work hours to maintain productivity. Additionally, companies should mandate the use of Virtual Private Networks (VPNs) when employees access corporate resources remotely, thereby enhancing information protection protocols.
The importance of stringent protective measures is emphasized by Intelligent Technical Solutions, which asserts,
If you want your confidential information to stay that way, you need to implement strict controls and policies on all devices that contain or have access to it.
Moreover, recent updates emphasize that organizations are increasingly implementing multi-factor authentication as part of their device protection protocols in 2024, indicating a rising trend towards improved information safeguarding. Establishing a structured procedure for reporting lost or stolen devices can greatly reduce the risk of security breaches. By articulating these clear usage expectations, organizations not only strengthen their protective stance but also promote increased productivity and compliance with regulatory standards. This proactive method is additionally backed by results that show educated workers are less inclined to jeopardize sensitive information, as illustrated in training programs centered on device protection.
Integrating Compliance and Security into Laptop Policies
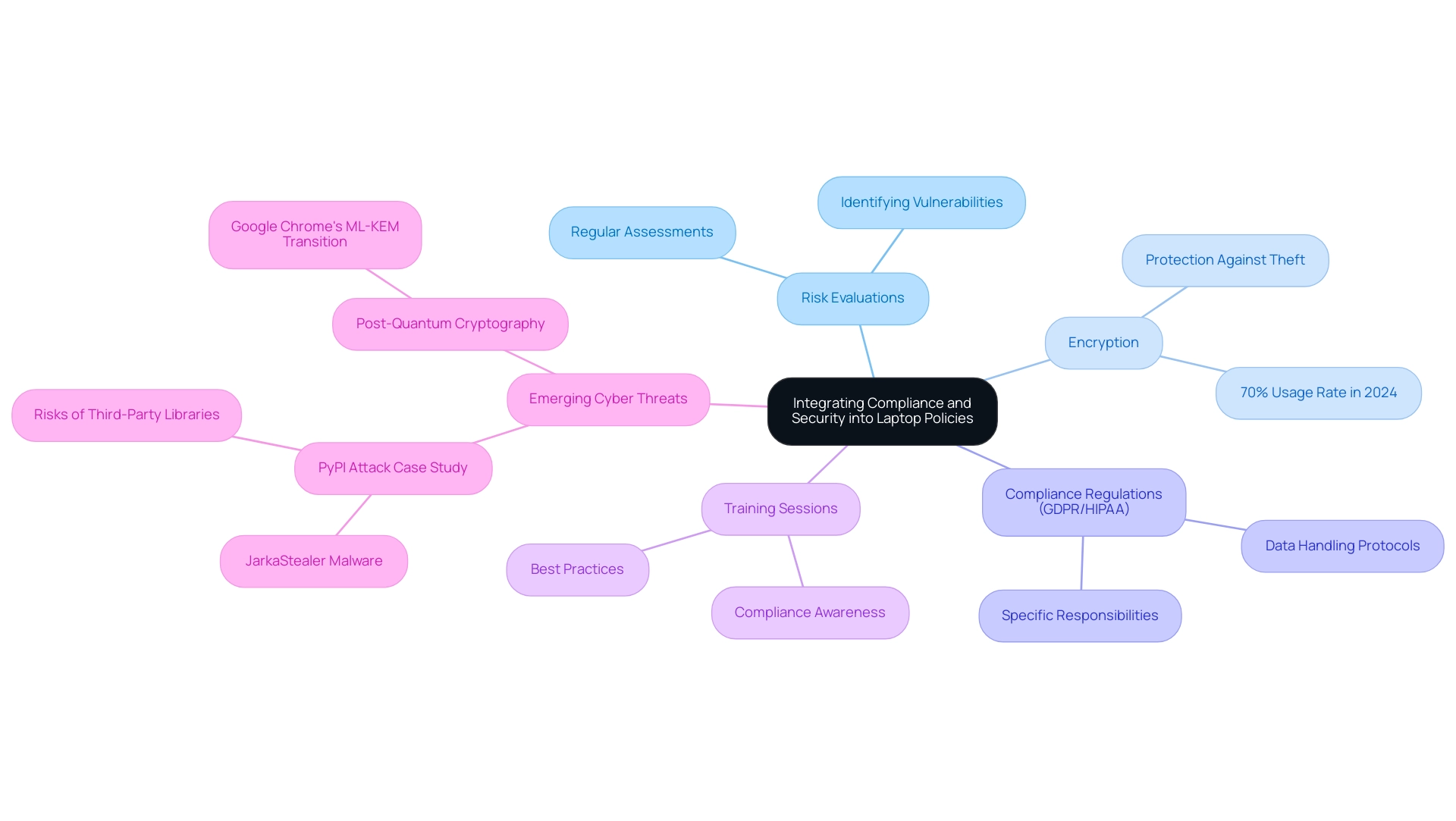
To effectively protect company information, it is essential to incorporate compliance and security measures into device policies. Regular risk evaluations should be carried out to identify vulnerabilities related to computer usage. Implementing encryption for information stored on portable computers is essential, ensuring that sensitive details remain protected even in instances of theft. In a landscape where encryption usage rates in corporate devices have reached approximately 70% in 2024, organizations must also include provisions for regular software updates and protective patches as a defense against evolving cyber threats.
Policies must explicitly address compliance with regulations such as GDPR and HIPAA, delineating specific responsibilities for personnel in terms of data handling. Moreover, cybersecurity specialists highlight the importance of training sessions on compliance and best practices, fostering a culture of awareness and responsibility among employees. As Riaan Olivier, Head of Global Managed Infrastructure at Striata, notes,
We were very quickly able to realize a positive ROI
from such initiatives. By prioritizing adherence and safety within device policies, organizations can significantly reduce risks and safeguard their assets. For example, the recent PyPI attack, in which Jarka Stealer malware was sent via compromised Python libraries, underscores the dangers related to third-party libraries and the necessity of verifying software sources. Moreover, with Google Chrome's forthcoming transition to ML-KEM for post-quantum cryptography protection, organizations should remain updated on developing protective measures that could affect their data encryption strategies. This comprehensive method aligns with current trends in device compliance policies and addresses the compliance statistics for 2024.
Implementing Remote Work Security Measures
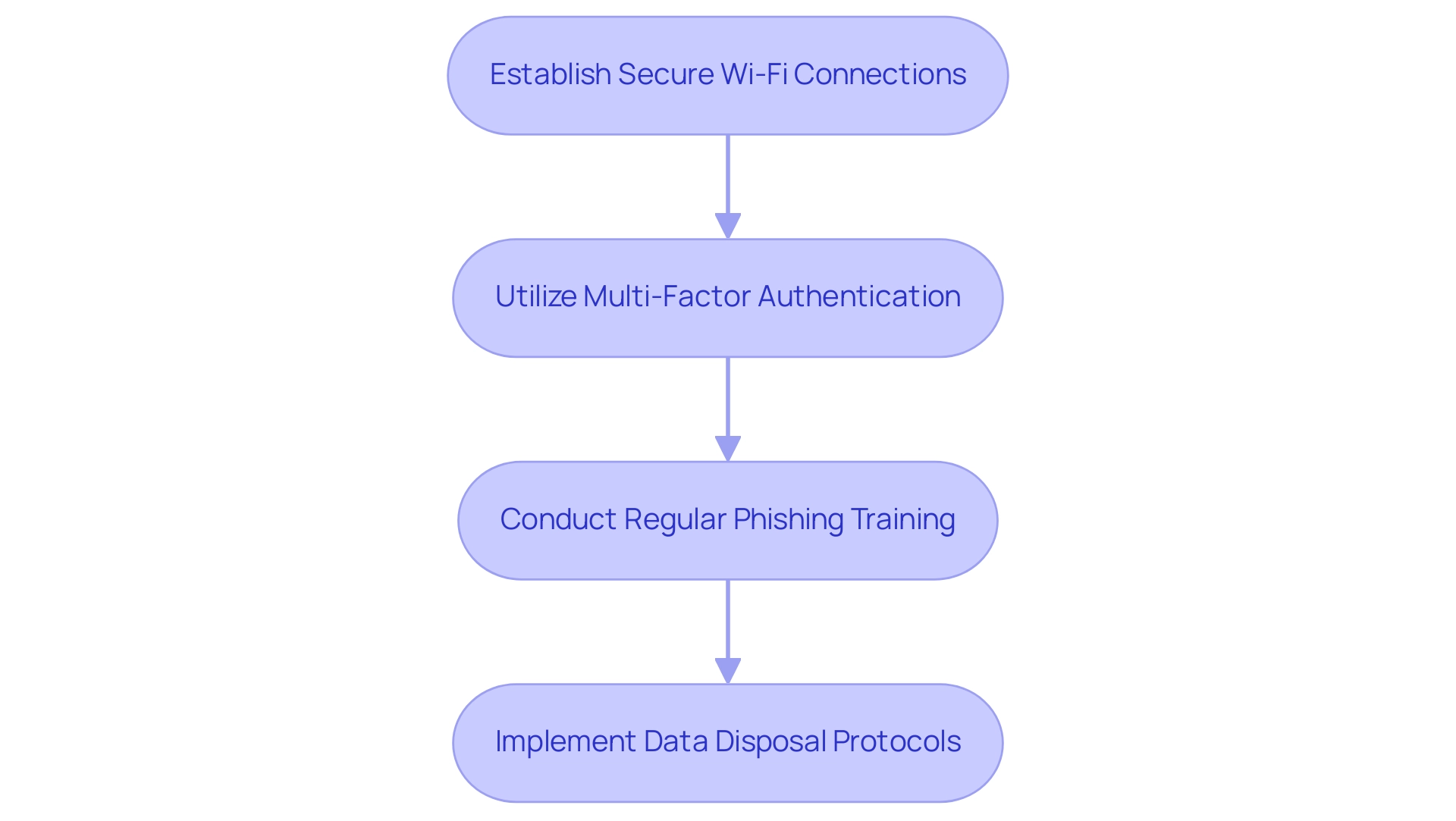
As remote work becomes increasingly common, organizations must implement specific protective measures for laptops used outside the office. This involves establishing secure Wi-Fi connections by urging staff to steer clear of public networks and utilize personal hotspots when feasible. Organizations should provide remote access tools that incorporate multi-factor authentication (MFA) to enhance security when individuals connect to company resources.
Regular training on recognizing phishing attempts and other cyber threats should also be mandatory for remote workers. Furthermore, establishing a protocol for securely disposing of company data when staff members leave the organization is essential to prevent data leaks and ensure compliance with data protection laws.
Regular Audits and Compliance Checks
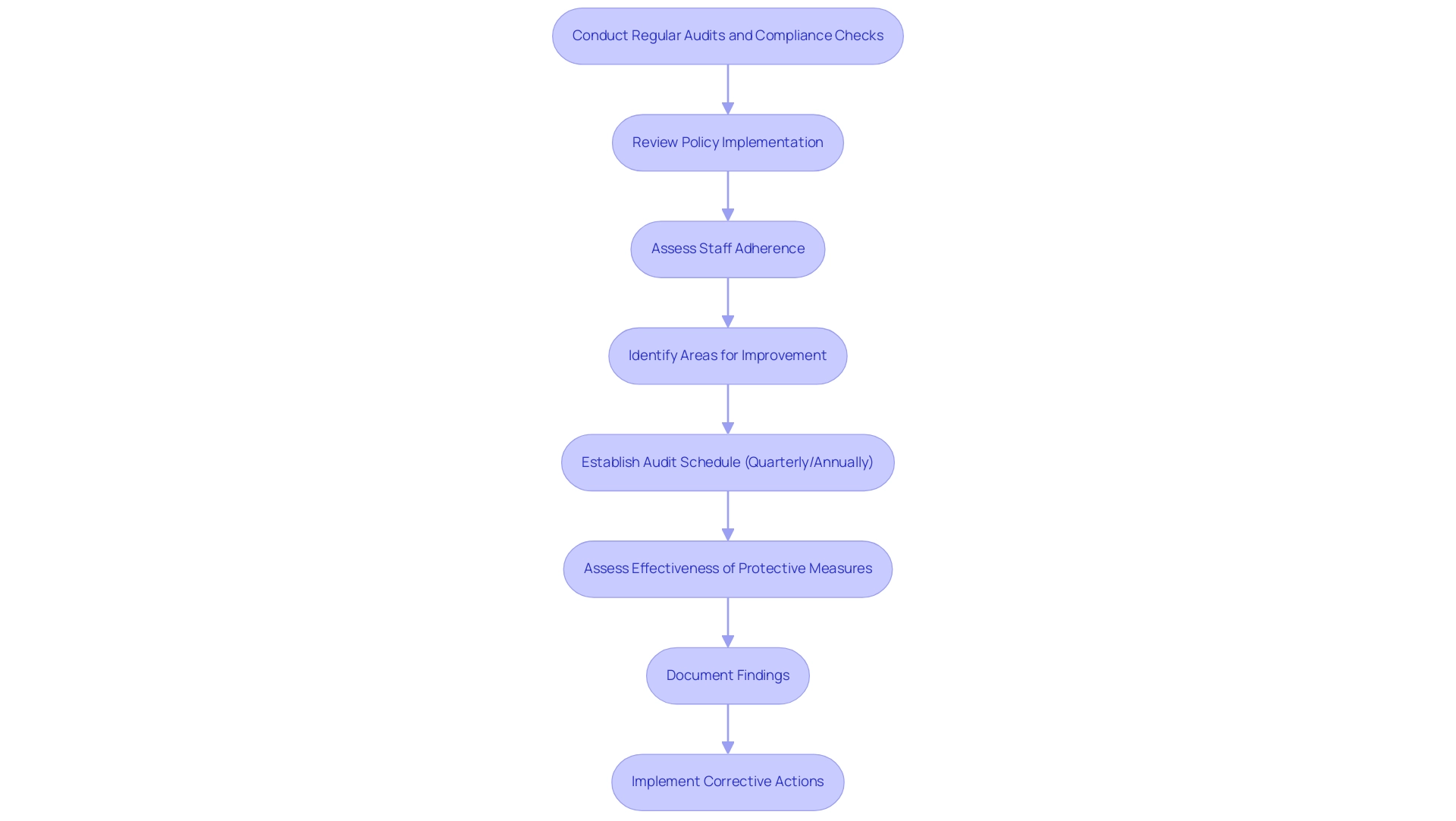
To maintain the effectiveness of laptop policies, organizations should conduct regular audits and compliance checks. This involves:
- Reviewing the implementation of policies
- Assessing staff adherence
- Identifying any areas for improvement
Establishing a schedule for these audits—whether quarterly or annually—can help organizations stay ahead of potential compliance issues. During audits, companies should assess the effectiveness of protective measures in place and update them as necessary to adapt to evolving threats. Additionally, documenting audit findings and implementing corrective actions ensures continuous improvement and accountability within the organization.
Fostering Employee Awareness and Engagement
To foster a culture of adherence and safety, organizations should actively engage staff in the creation and enforcement of laptop policies. This can be accomplished through:
- Workshops
- Feedback sessions that enable staff to express their concerns and suggestions
Regular communication about the importance of adhering to these policies can also reinforce their relevance. Organizations might consider:
- Creating a dedicated team
- Assigning security champions within departments to promote best practices and act as points of contact for questions or concerns
By fostering employee awareness and engagement, organizations can enhance the effectiveness of their laptop policies and create a more secure working environment.
Conclusion
Establishing robust laptop usage policies is paramount for organizations navigating the complexities of modern cybersecurity threats. By clearly defining acceptable behaviors and implementing stringent security measures, companies can effectively protect sensitive data while fostering a culture of compliance and awareness among employees. Key components such as the prohibition of unauthorized software installation, the requirement for VPN usage, and the implementation of multi-factor authentication serve to fortify organizational defenses against data breaches.
Moreover, integrating compliance measures into these policies is essential. Regular risk assessments, data encryption, and adherence to regulations like GDPR and HIPAA ensure that organizations remain vigilant against potential vulnerabilities. Training sessions focused on security best practices further empower employees, reinforcing their role in safeguarding corporate assets.
As remote work continues to rise, implementing specific security protocols for laptops used outside the office becomes increasingly critical, ensuring that employees are equipped to navigate potential risks.
Regular audits and compliance checks are vital for maintaining the effectiveness of these policies. By evaluating adherence and updating security measures in response to evolving threats, organizations can ensure continuous improvement and accountability. Engaging employees in the policy development process not only enhances compliance but also fosters a culture of security awareness, ultimately leading to a more secure working environment.
In summary, the establishment of comprehensive laptop usage policies is not merely a precaution but a strategic necessity for organizations. By prioritizing security, compliance, and employee engagement, companies can navigate the digital landscape with confidence, safeguarding their critical data and maintaining operational efficiency in an increasingly remote work world.




