Introduction
In an age where cyber threats loom larger than ever, organizations are compelled to fortify their defenses through proactive measures such as penetration testing. This essential practice, often referred to as ethical hacking, simulates real-world attacks to identify vulnerabilities within systems before they can be exploited by malicious actors.
With staggering statistics revealing that businesses lose approximately $17,700 every minute to phishing attacks, the urgency for effective security assessments is undeniable. As companies increasingly adopt advanced technologies, including artificial intelligence, to enhance their cybersecurity frameworks, understanding the nuances of penetration testing becomes critical.
This article delves into the various aspects of penetration testing, from its fundamental importance and the selection of qualified providers to the diverse testing methodologies available. By exploring these dimensions, organizations can better equip themselves to navigate the complex landscape of cybersecurity and safeguard their valuable assets.
Understanding Penetration Testing: Definition and Importance
Penetration assessment, commonly known as ethical hacking, serves as a critical defense mechanism against cyber threats by simulating attacks on computer systems to uncover exploitable vulnerabilities. As cyber attacks become increasingly prevalent, with organizations experiencing a loss of $17,700 every minute due to phishing attacks, the importance of these assessments cannot be overstated. Regular penetration testing, performed by the best penetration testing service providers, allows businesses to proactively identify and address vulnerabilities before they can be exploited by malicious actors.
In 2024, 51% of businesses are leveraging AI to enhance their cybersecurity initiatives, highlighting a trend towards more advanced protective measures. This proactive approach not only assists entities in safeguarding sensitive data but also helps maintain customer trust and compliance with regulatory standards. Moreover, with 78% of financial service firms reporting security breaches, the financial sector demonstrates the need for the best penetration testing service providers to establish strict vulnerability assessment protocols.
The financial consequences of insufficient security assessments are considerable, with data breach expenses averaging USD 5.97 million for these entities. By implementing these practices, entities can significantly enhance their cybersecurity frameworks, ultimately translating to reduced data breach costs and improved resilience against evolving threats. Furthermore, vulnerability assessments tackle a diverse array of cybersecurity concerns, such as malware, ransomware, and social engineering, guaranteeing a comprehensive defense strategy.
Key Factors to Consider When Choosing a Penetration Testing Provider
Selecting the right penetration testing provider is a critical decision that organizations must approach with a comprehensive understanding of several key factors:
-
Experience and expertise are essential when choosing from the best penetration testing service providers, especially one that has a solid track record in penetration assessment within your industry. The depth of knowledge and relevant experience can significantly influence the effectiveness of the assessment.
-
Range of Services: It is essential to evaluate whether the provider offers a complete range of services, including web application, network, and mobile application evaluations. A diversified service offering from the best penetration testing service providers ensures that all potential vulnerabilities are covered, providing a holistic security posture.
-
Methodology: It is essential to confirm that the best penetration testing service providers comply with established methodologies, such as OWASP or NIST, to ensure that rigorous evaluation practices are followed. This adherence not only enhances the reliability of the findings but also aligns with industry standards.
-
In your selection process, focusing on the quality of reporting is crucial when considering the best penetration testing service providers. A reputable provider will deliver detailed and actionable reports that not only outline the identified vulnerabilities but also recommend effective remediation strategies.
-
Post-Test Support: The best penetration testing service providers offer post-test support, including comprehensive reports and remediation assistance for identified vulnerabilities. This ongoing support can be crucial for organizations looking to effectively manage and mitigate risks.
-
Cost: While the cost should not be the sole determining factor, it remains essential to align the services offered with your budget. According to estimates from ScienceSoft, businesses can anticipate spending approximately $5,000 for black box assessments of essential web applications covering up to 10 IP addresses. However, it is imperative to ensure that this pricing from the best penetration testing service providers reflects quality and comprehensiveness without embedding excessive contingency costs, as noted by cybersecurity expert Chad Kime:
Customers certainly prefer the certainty of flat-rate, standardized pricing, but often overlook the reality that in addition to strictly limited tests, the vendor typically also needs to embed contingency costs into the pricing.
-
Threat-Led Assessment (TLPT): Recent advancements in threat-led assessment, especially concerning the latest regulatory technical draft set for DORA, should also be taken into account. This approach focuses on real-world threats and can provide a more targeted assessment of vulnerabilities.
Incorporating these considerations into your selection process will enhance your organization's cybersecurity defenses and ensure effective vulnerability management by engaging the best penetration testing service providers. For additional insights, the case study titled "Cybersecurity Risk Assessment – A Complete Guide" offers methodologies for evaluating and handling cybersecurity risks pertinent to security assessments.
Exploring Different Types of Penetration Testing Services
Organizations today can choose from a varied selection of services offered by the best penetration testing service providers, customized to their specific protection requirements. These include:
-
Black Box Testing: In this approach, testers operate without prior knowledge of the system, simulating the tactics of an external adversary.
This method is particularly valuable for identifying vulnerabilities that may be exploited by real-world attackers. -
White Box Testing: Here, testers are provided with complete information about the system, enabling a thorough examination of internal vulnerabilities.
This thorough viewpoint is crucial for revealing possible vulnerabilities that might be missed in alternative evaluation methods. As noted by cybersecurity experts, understanding both external and internal risks is critical to a robust security posture. -
Gray Box Testing: This hybrid method combines elements of both black and white box testing. Testers possess limited knowledge of the system, reflecting the perspective of a user with restricted access.
This approach is effective for identifying vulnerabilities that might be exploited by insiders or through social engineering tactics. -
Web Application Testing: This specialized service concentrates on identifying weaknesses within web applications, which are increasingly targeted by cybercriminals.
With threats evolving, entities must prioritize securing their web applications to protect sensitive data and maintain user trust.
Significantly, the OWASP Top 10 Mobile Security Risks emphasizes that insecure data storage is the most common risk, accounting for 27% of threats, highlighting the need for strong protective measures in mobile app development. -
Network Penetration Testing: This service evaluates the protection of a company’s network framework, identifying possible access points for intruders.
Comprehending these unique forms of assessment services is crucial as organizations plan to align their evaluation initiatives with the best penetration testing service providers to achieve broader security goals.
As worldwide expenditure on cybersecurity products and services is expected to total $1.75 trillion cumulatively from 2021 to 2025, investing in these evaluation methodologies is becoming increasingly vital for sustaining a robust defensive stance against cyber threats.
Furthermore, with 40% of security assessments performed for returning clients and 29% of targets recognized with critical weaknesses, the continuous necessity for such evaluations is evident.
The Role of Certifications and Accreditations in Penetration Testing
Certifications and accreditations are essential for guaranteeing the effectiveness and credibility of security assessment services. As the landscape of cybersecurity evolves, so does the necessity for professionals to validate their skills through recognized certifications. Key certifications to consider include:
- Certified Ethical Hacker (CEH): This certification validates the essential knowledge and skills required for ethical hacking practices, ensuring professionals can effectively identify vulnerabilities.
- Offensive Security Certified Professional (OSCP): Celebrated for its demanding practical approach, the OSCP acknowledges professionals who can showcase real-world exploitation skills and techniques.
- CompTIA PenTest+: This certification encompasses the critical skills needed for penetration testing and vulnerability assessment, making it a foundational credential for aspiring ethical hackers.
- ISO/IEC 27001 Certification: This internationally acknowledged standard highlights an organization’s commitment to information protection management, reinforcing its dedication to maintaining high safety protocols.
With 30% of data breaches involving authenticated users, as noted in industry reports, the relevance of these certifications cannot be overstated. They not only bolster a provider's credibility but also ensure that professionals remain abreast of the latest security trends and practices.
Furthermore, involvement in professional cybersecurity communities is essential for the continuous learning and growth of security testers, enabling them to exchange knowledge and remain informed about emerging threats. The global market for cybersecurity software and services is projected to exceed $19 billion in 2024, underscoring the increasing demand for skilled professionals equipped with these essential certifications.
How to Evaluate and Compare Penetration Testing Companies
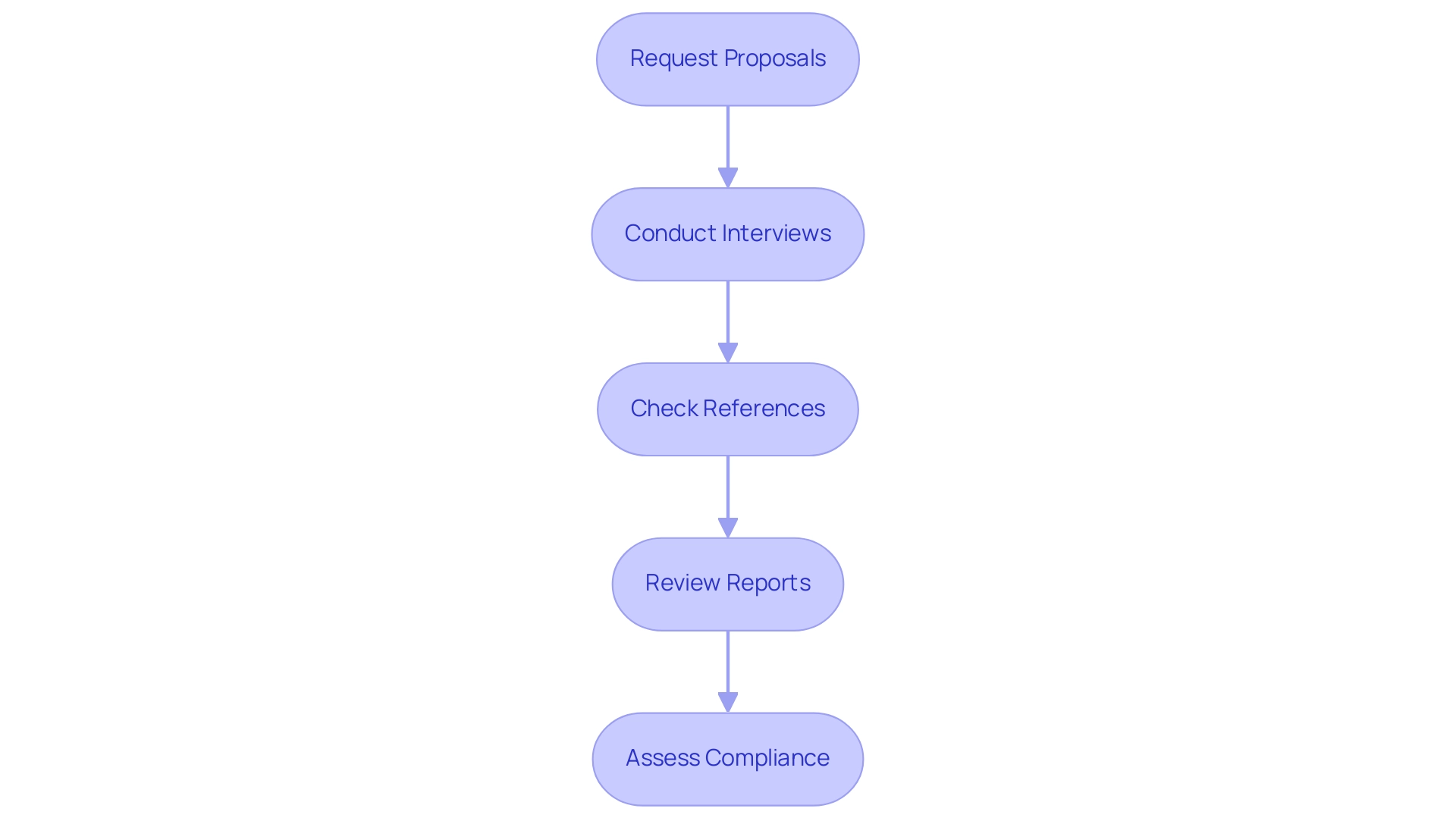
To effectively assess and contrast security assessment firms, entities should follow the ensuing organized method:
- Request Proposals: Initiate the process by gathering detailed proposals from multiple providers. This will provide insights into their service offerings, methodologies, and pricing structures, allowing for a comprehensive understanding of the market landscape. As the cybersecurity market in the UK has seen growth from 1,838 companies in 2022 to over 2,091 in 2024, understanding the variety of options available is crucial.
- Conduct Interviews: Engage directly with potential providers through interviews. This interaction is critical for assessing their understanding of your specific requirements and their strategic approach to penetration testing. Organizations should consider whether a boutique firm, which may offer personalized service, or a larger provider, known for extensive resources and capabilities, better suits their requirements.
- Check References: Request case studies or references from previous clients. By analyzing these testimonials, companies can assess the provider's effectiveness, track record, and dependability in delivering strong protective solutions. For instance, NTT Data is noted for its global reach and emphasis on enterprise security, providing a model for evaluating effectiveness.
- Review Reports: Analyze sample reports from past engagements. Assessing the clarity, detail, and actionable insights of these reports is essential to understanding how the provider communicates findings and recommendations. Larger providers often have standardized reporting formats, while boutique firms may provide more tailored insights.
- Assess Compliance: Verify that the provider adheres to relevant regulations and standards applicable to your entity. Compliance is not just a legal obligation; it is a fundamental aspect of ensuring that the services align with industry best practices, especially when considering the best penetration testing service providers. As Ihor Sasovets, Lead Protection Engineer at TechMagic, emphasizes,
By investing in these proactive protective measures, companies can prevent costly incidents, safeguard their data, and maintain customer trust, ultimately saving millions in the long run.
This strategic evaluation process not only enhances security posture but also contributes to long-term business resilience.
Conclusion
The importance of penetration testing in today’s cybersecurity landscape cannot be overstated. As organizations face escalating cyber threats and significant financial losses due to breaches, the implementation of robust penetration testing practices serves as a vital line of defense. By simulating real-world attacks, businesses can proactively identify and remediate vulnerabilities, thereby safeguarding sensitive data and maintaining compliance with regulatory standards.
Choosing the right penetration testing provider is equally critical. Organizations must consider factors such as:
- Experience
- Service range
- Adherence to established methodologies
- Quality of reporting
A thorough evaluation of potential providers ensures that businesses can select a partner capable of delivering effective security assessments tailored to their specific needs. The diverse types of testing services available—ranging from black box to web application testing—further highlight the necessity of aligning testing strategies with overarching security objectives.
Additionally, the role of certifications and accreditations in enhancing the credibility of penetration testing cannot be overlooked. Qualified professionals equipped with recognized certifications are essential for delivering high-quality assessments that reflect the latest industry practices. As the cybersecurity landscape continues to evolve, ongoing education and professional development remain crucial for maintaining a skilled workforce.
In conclusion, investing in comprehensive penetration testing not only mitigates risks but also fortifies an organization’s overall security posture. As businesses navigate the complexities of cybersecurity, prioritizing these assessments will ultimately contribute to long-term resilience against evolving threats, ensuring the protection of valuable assets and the trust of customers.




